Intel® Packet Protect User’s Guide
26
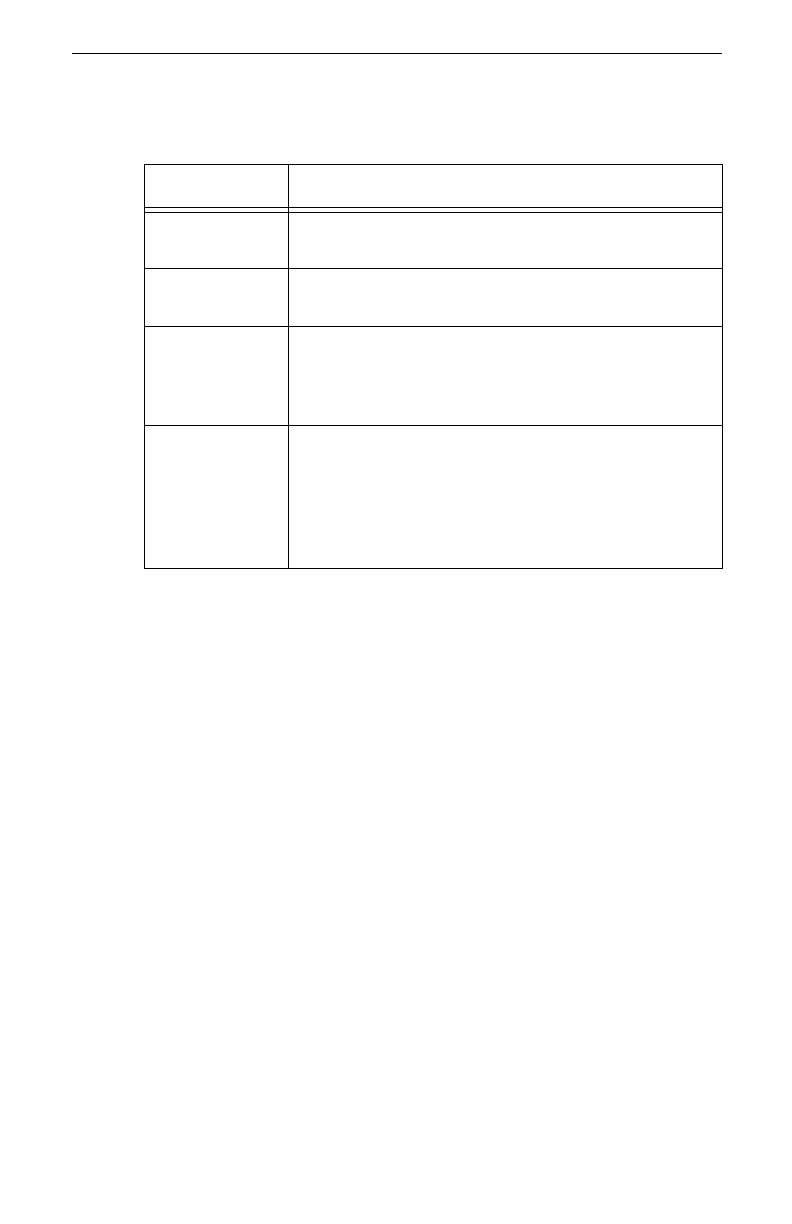
Every rule contains the information described in the following table.
Note
: All rules specify All IP for the Traffic Group. If a rule is applied,
the security settings apply to all IP traffic between the two
computers communicating. Refer to the readme file on the
product CD-ROM for a list of ports and protocols that are
always sent unprotected in order for Packet Protect to func-
tion.
The Default Rule
When you install Packet Protect, the default rule is created. The Default Rule
has these properties:
Table 4: Rule Settings
Rule Setting Description
Destination
workgroup
Collection of computers with which a computer
communicates.
Security action Collection of security settings used when negotiating a
communication.
Rule failure Definition of what happens when the rule is applied,
but the communication is not negotiated successfully.
You can allow the communication to occur unsecured,
or deny the communication.
Authentication Definition of how your computer verifies the other
computer’s pre-shared key when the rule is applied.
You can use the authentication settings already
specified for your computer (on the Security tab), or
use custom settings for the rule (propose a pre-shared
key).
• Destination Workgroup Everybody.
Applies to every computer in the LAN.
• Security Action Default Action.
The standard security action, which uses a
time limit of 8 hours. Refer to “Customize
Security Actions” on page 33 for detailed
information about security actions.


















