EtherFast
®
Cable/DSL Firewall Router with 4-Port Switch/VPN Endpoint
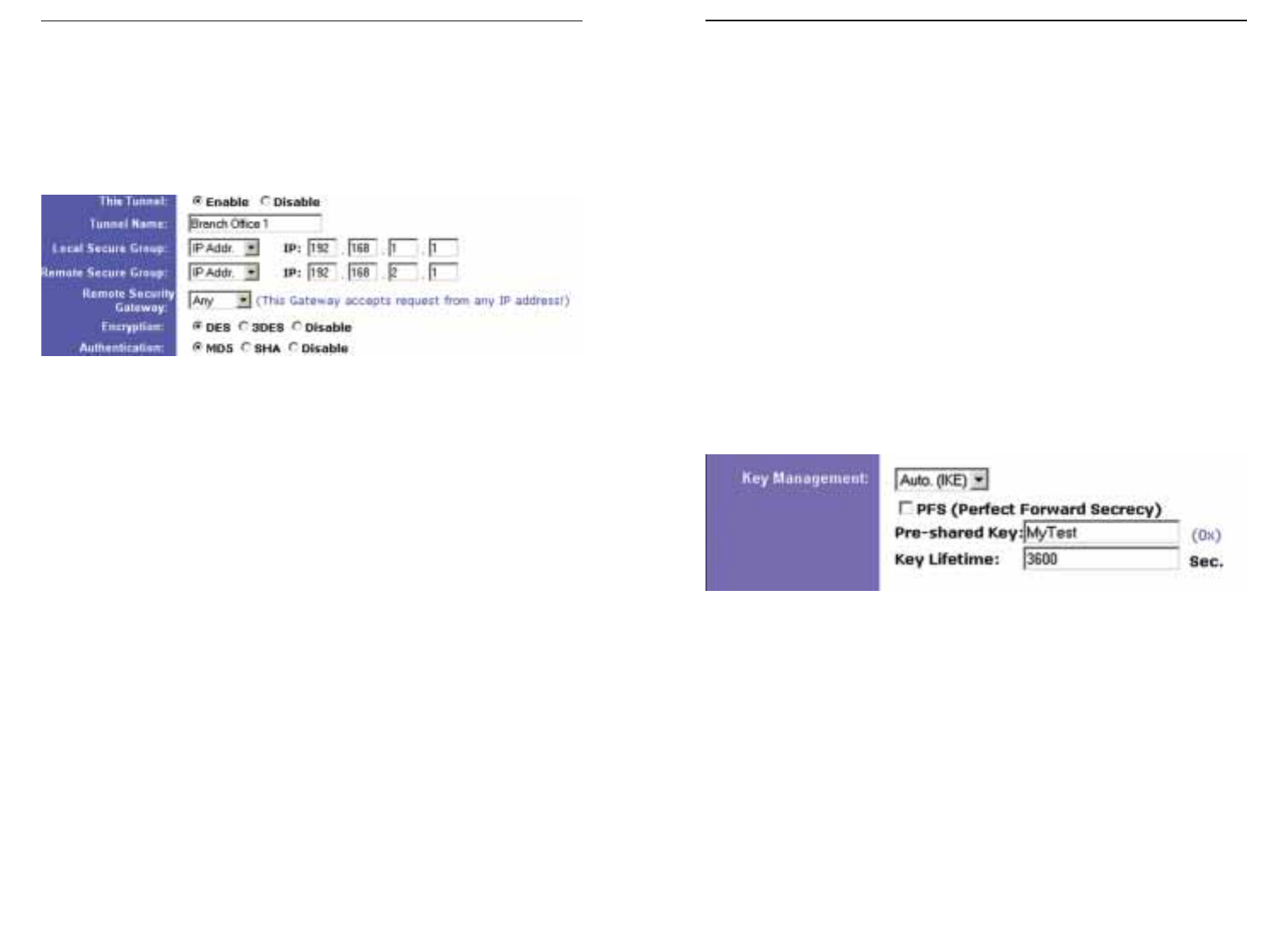
Key Management
In order for any encryption to occur, the two ends of the tunnel must agree on
the type of encryption and the way the data will be decrypted. This is done by
sharing a “key” to the encryption code. Under Key Management, you may
choose automatic or manual key management.
Automatic Key Management
Select Auto (IKE) and enter a series of numbers or letters in the Pre-shared Key
field. Check the box next to PFS (Perfect Forward Secrecy) to ensure that the
initial key exchange and IKE proposals are secure. In the example shown in
Figure 7-20, the word MyTest is used. Based on this word, which MUST be
entered at both ends of the tunnel if this method is used, a key is generated to
scramble (encrypt) the data being transmitted over the tunnel, where it is
unscrambled (decrypted). You may use any combination of up to 24 numbers or
letters in this field. No special characters or spaces are allowed. In the Key
Lifetime field, you may optionally select to have the key expire at the end of a
time period of your choosing. Enter the number of seconds you’d like the key to
be useful, or leave it blank for the key to last indefinitely.
Manual Key Management
Similarly, you may choose Manual keying, which allows you to generate the
key yourself. Enter your key into the Encryption KEY field. Then enter an
Authentication KEY into that field. These fields must both match the infor-
mation that is being entered in the fields at the other end of the tunnel. The
example in Figure 7-21 shows some sample entries for both the Encryption and
Authentication Key fields. Up to 24 alphanumeric characters are allowed to
create the Encryption Key. Up to 20 alphanumeric characters are allowed to
create the Authentication Key.
4544
Figure 7-20
Instant Broadband
®
Series
• Any - If you select Any for the Remote Security Gateway, as shown in
Figure 7-19, the VPN device at the other end of the tunnel will accept a
request from any IP address. The remote VPN device can be another
Firewall Router, a VPN Server, or a computer with VPN client software
that supports IPSec. If the remote user has an unknown or dynamic IP
address (such as a professional on the road or a telecommuter using
DHCP or PPPoE), then Any should be selected.
Encryption
Using Encryption also helps make your connection more secure. There are
two different types of encryption: DES or 3DES (3DES is recommended
because it is more secure). You may choose either of these, but it must be the
same type of encryption that is being used by the VPN device at the other end
of the tunnel. Or, you may choose not to encrypt by selecting Disable.
Authentication
Authentication acts as another level of security. There are two types of authen-
tication: MD5 and SHA (SHA is recommended because it is more secure). As
with encryption, either of these may be selected, provided that the VPN device
at the other end of the tunnel is using the same type of authentication. Or, both
ends of the tunnel may choose to Disable authentication.
Figure 7-19


















