IDL series User Guide
700
Appendix C --- IEEE 802.1x protocol over IP DSLAM
Understanding How 802.1X Authentication Works
IEEE 802.1X is a client-server-based access control and authentication protocol that
restricts unauthorized devices from connecting to a local area network (LAN) through
publicly accessible ports. 802.1X authenticates each user device that is connected to a
switch port before making available any services that are offered by the switch or the LAN.
Until the device is authenticated, 802.1X access control allows only Extensible
Authentication Protocol over LAN (EAPOL) traffic through the port to which the device is
connected. After authentication is successful, normal traffic can pass through the port.
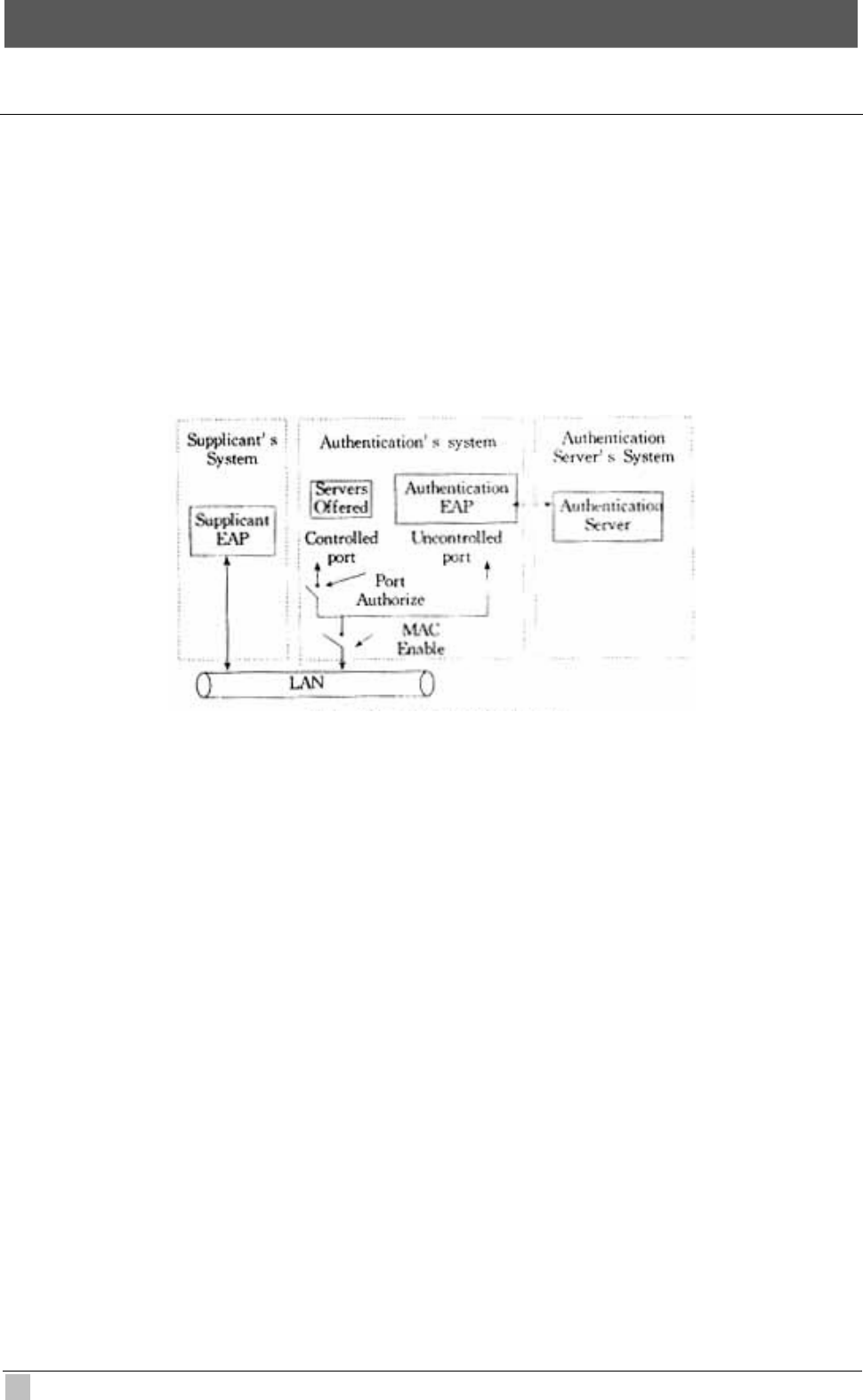
802.1X controls network access by creating two distinct virtual access points at each port
(See Above Figure). One access point is an uncontrolled port; the other is a controlled port.
All traffic through the single port is available to both access points. Only EAPOL traffic is
allowed to pass through the uncontrolled port, which is always open. The controlled port is
open only when the device that is connected to the port has been authorized by 802.1X.
After this authorization takes place, the controlled port opens, allowing normal traffic to
pass.


















