ZyWALL 10/50 Internet Security Gateway
28-2 IPSec Log
28.2 VPN Responder IPSec Log
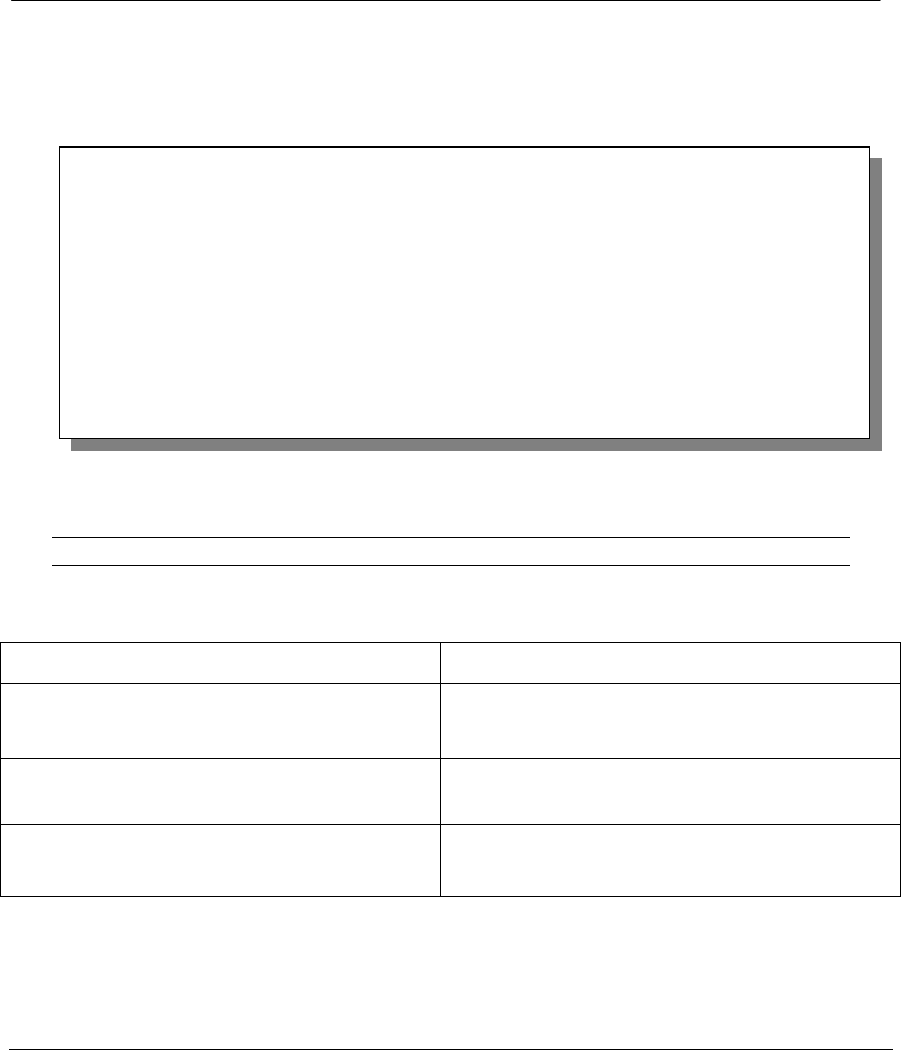
The following figure shows a typical log from the VPN connection peer.
Figure 28-2 Example VPN Responder IPSec Log
This menu is useful for troubleshooting. A log index number, the date and time the log was created and a log
message are displayed.
Double exclamation marks (!!) denote an error or warning message.
The following table shows sample log messages during IKE key exchange.
Table 28-1 Sample IKE Key Exchange Logs
LOG MESSAGE DESCRIPTION
Cannot find outbound SA for rule <#d>
The packet matches the rule index number (#d), but
Phase 1 or Phase 2 negotiation for outbound (from the
VPN initiator) traffic is not finished yet.
Send Main Mode request to <IP>
Send Aggressive Mode request to <IP>
The ZyWALL has started negotiation with the peer.
Recv Main Mode request from <IP>
Recv Aggressive Mode request from <IP>
The ZyWALL has received an IKE negotiation request
from the peer.
Index: Date/Time: Log:
------------------------------------------------------------
001 01 Jan 08:08:07 Recv Main Mode request from <192.168.100.100>
002 01 Jan 08:08:07 Recv:<SA>
003 01 Jan 08:08:08 Send:<SA>
004 01 Jan 08:08:08 Recv:<KE><NONCE>
005 01 Jan 08:08:10 Send:<KE><NONCE>
006 01 Jan 08:08:10 Recv:<ID><HASH>
007 01 Jan 08:08:10 Send:<ID><HASH>
008 01 Jan 08:08:10 Phase 1 IKE SA process done
009 01 Jan 08:08:10 Recv:<HASH><SA><NONCE><ID><ID>
010 01 Jan 08:08:10 Start Phase 2: Quick Mode
011 01 Jan 08:08:10 Send:<HASH><SA><NONCE><ID><ID>
012 01 Jan 08:08:10 Recv:<HASH>
Clear IPSec Log (y/n):