177
addresses. Aggressive mode reduces this process to three messages, but parameter
negotiation is limited, identity protection is lacking except when using public key
encryption, and is more vulnerable to Denial of Service attacks.
Phase II, known as Quick Mode, establishes symmetrical IPSec Security
Associations for both AH and ESP. It does this by negotiating IPSec parameters,
exchange nonces to derive session keys from the IKE shared secret, exchange DH
values to generate a new key, and identify which traffic this SA bundle will protect
using selectors (IDi and IDr payloads).
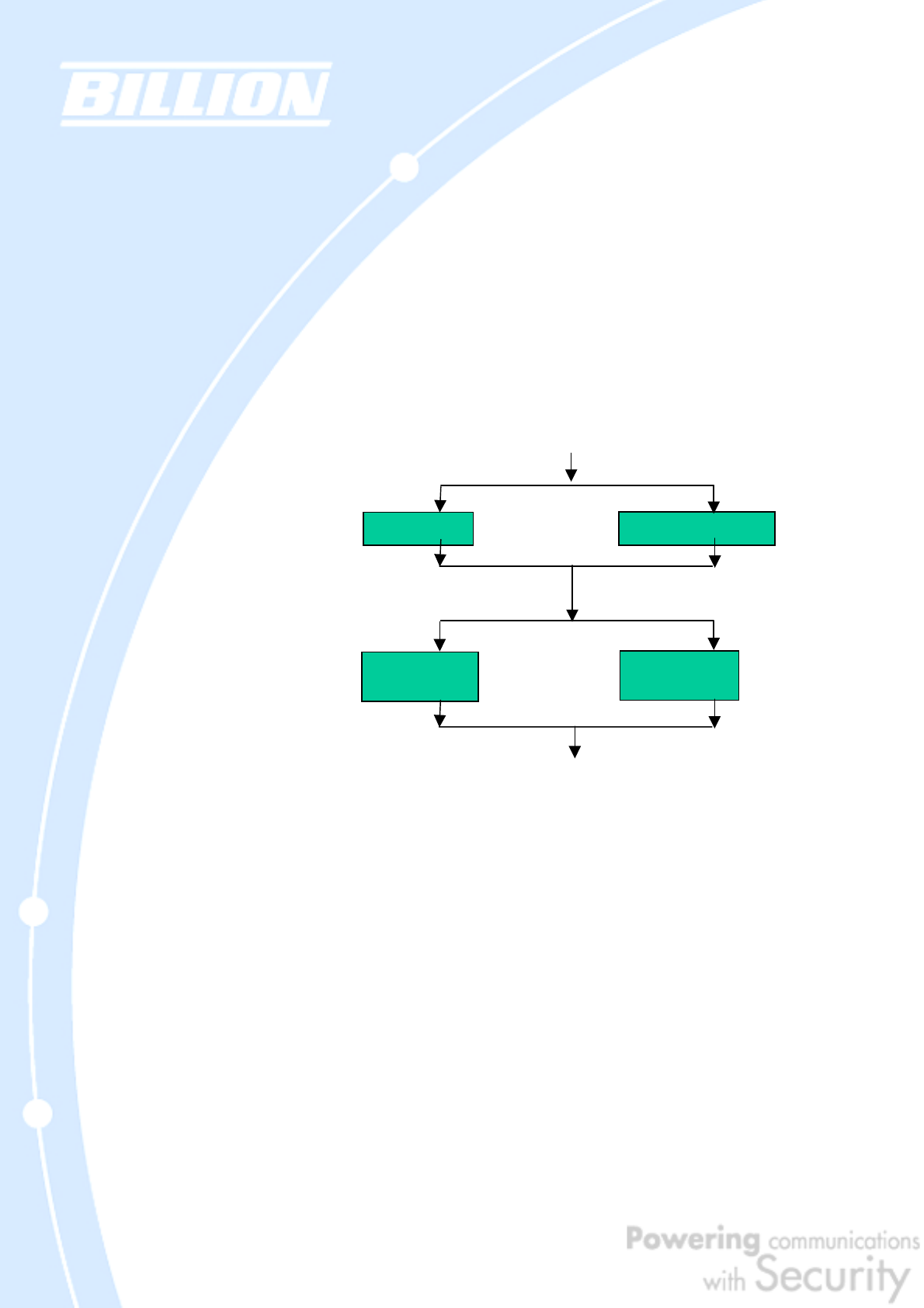
The following is an illustration on how data is handled with IKE:
Start
Main Mode
A
gg
ressive Mode
Quick Mode
With PFS
Quick Mode
Without PFS
Phase 1
Negotiate
ISAKMP SA
Mutual Authentication
Phase 2
Negotiate SAs
For AH and ESP
Protected Data Transfe
r
New IPSec tunnel or Rekeying
or
or


















