DGS-3100 Series Gigabit Stackable Managed Switch User Manual
Defining Application Authentication Settings
Application Authentication permits network administrators to assign authentication methods for user authentication. For
example, console users can be authenticated by Authentication List 1, while Telnet users are authenticated by
Authentication List 2.
1. Click Security > Access Authentication Control > Application Authentication Settings. The
Application
Authentication Settings Page
opens:
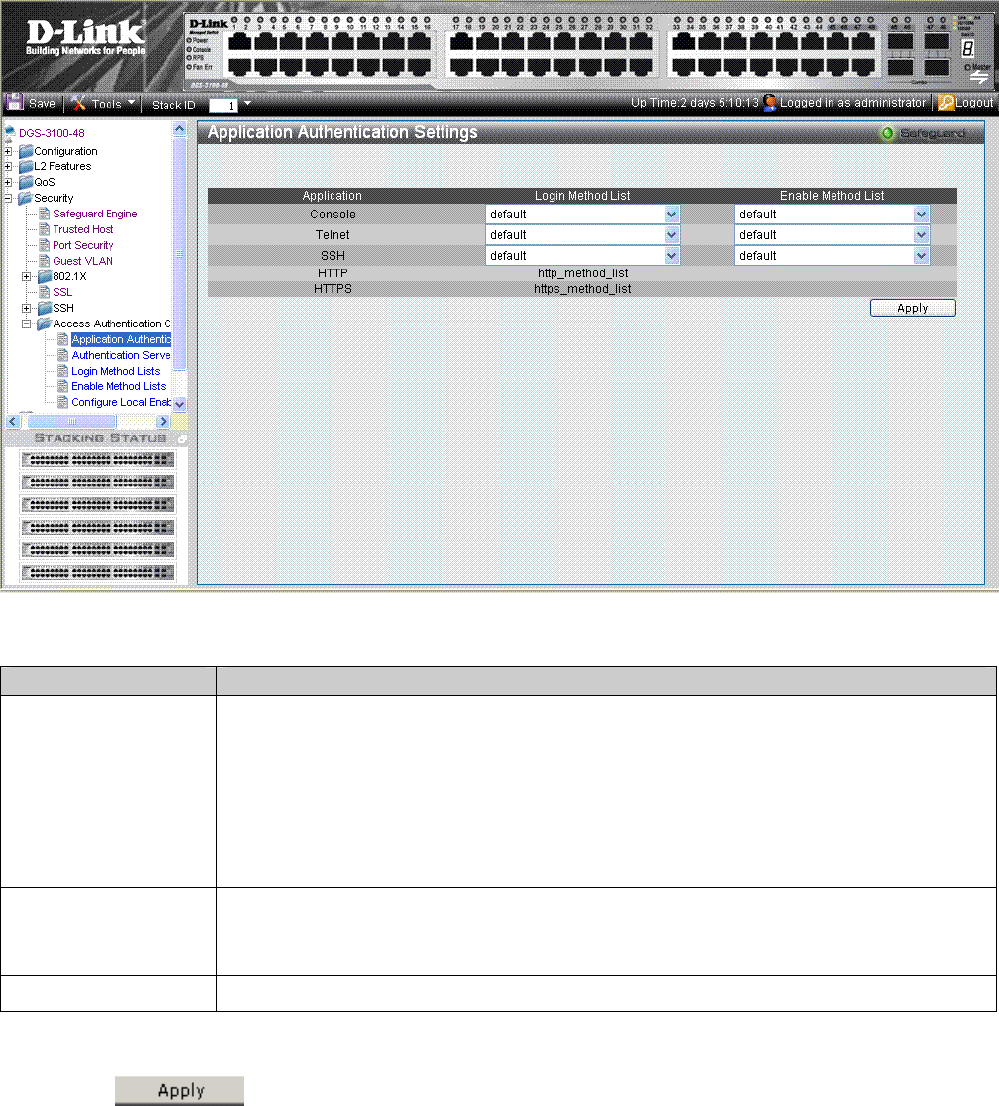
Figure 5-17. Application Authentication Settings Page
The
Application Authentication Settings Page contains the following fields:
Field Description
Application
Indicates the authentication application for which the Login Method or Enable Method lists
are defined. The possible field values are:
Console — Indicates that Authentication profiles are used to authenticate console users.
Telnet — Indicates that Authentication profiles are used to authenticate Telnet users.
Secure Telnet (SSH) — Indicates that Authentication profiles are used to authenticate
Secure Shell (SSH) users. SSH provides clients secure and encrypted remote connections
to a device.
Login Method List
Defines the method used by the application to authenticate normal login.
http_method_list and https_method_list are fixed method names for http and https
respectively.
Enable Method List
Defines the method used by the application to enable a normal login.
2. Select the login method for the Console, Telnet, and Secure Telnet (SSH ) from the list under Login Method List.
3. Select the enable method for the Console, Telnet, and Secure Telnet (SSH ) from the list under Enable Method List.
4. Click
. The Application Authentication settings are defined, and the device is updated.
113