DGS-3100 Series Gigabit Stackable Managed Switch User Manual
3. Click
.The Authentication Host properties are defined, and the device is updated.
• To edit an authentication, click
adjacent to the relevant IP Address on the list. The upper fields display the
current values, which then can be edited.
• To delete an authentication, click
adjacent to the relevant IP Address on the list. The Authentication Server
settings are defined, and the device is updated.
Defining Login Methods
Network users must first login to the device on the Login Method Lists Page. Access as non-administrative users is granted.
To configure the device as a Network Administrator, the user must also log on to the device on the
Enable Method Lists
Page
.
User authentication occurs in the order the methods are selected. If the first authentication method is not available, the next
selected method is used. For example, if the selected authentication method is RADIUS, Local, and the RADIUS server is
not available, the user is authenticated locally. To define the user only login method:
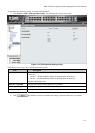
1. Click Security > Access Authentication Control > Login Method Lists. The
Login Method Lists Page opens:
Figure 5-19. Login Method Lists Page
The
Login Method Lists Page contains the following fields:
Field Description
Method List Name
Displays the method list name. The field is user-defined besides the http_method_list and
https_method_list which cannot be deleted or renamed.
Method 1
Indicates the first method used to authenticate the network user. The possible field values are:
RADIUS — User authentication occurs at the RADIUS server.
TACACS+ — The user authentication occurs at the TACACS+ server.
None — No user authentication occurs.
Local — User authentication occurs at the device level. The device checks the user name
and password for authentication.
Method 2
Indicates the second method used to authenticate the network user. The possible field values
115