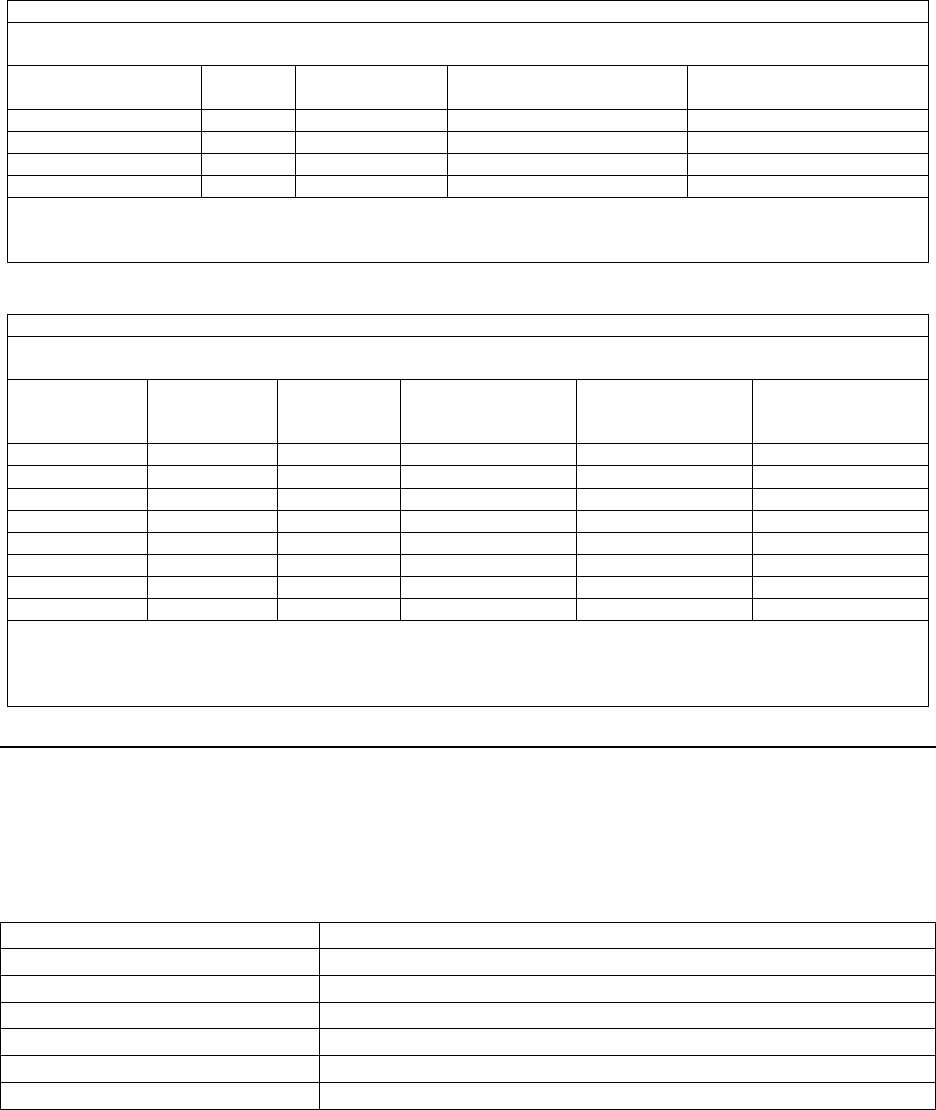
Notes:
y Transaction Length set at 1024 bytes
y See section 8.2 for Test Environment Information
35163204810SHA-1 / RSA
3012920481SHA-1 / RSA
2401,155102410SHA-1 / RSA
19790110241SHA-1 / RSA
JCE
(Transactions/Second)
i5/OS
(Transactions/Second)
RSA Key Length
(Bits)
Threads
Encryption
Algorithm
Signing Performance
Table 8.2
Notes:
y Key Length set at 1024 bits
y Transaction Length set at 16384 bytes
y See section 8.2 for Test Environment Information
78,659,5614,801132,059,8078,06010SHA-512
69,098,7314,217115,201,8007,0311SHA-512
75,925,6684,634132,301,8788,07510SHA-384
65,865,3274,020115,505,5487,0501SHA-384
39,184,9232,39273,086,4114,46110SHA-256
33,576,5232,04963,645,2283,8851SHA-256
48,401,7732,954178,172,75110,87510SHA-1
37,608,1722,295110,642,8966,7531SHA-1
JCE
(Bytes/Second)
JCE
(Transactions/
Second)
i5/OS
(Bytes/ Second)
i5/OS
(Transactions/
Second)
Threads
Encryption
Algorithm
Digest Performance
Table 8.3
8.4 Hardware Cryptographic API Performance
This section provides information on the hardware based cryptographic offload solution IBM 4764
PCI-X Cryptography Coprocessor (Feature Code 4806). This solution will improve the system CPU
capacity by offloading CPU demanding cryptographic functions.
IBM System i5
Platform Support
No IOP Required
Required Hardware
Secure hardware module
Cryptographic Key Protection
Secure accelerator (SSL)
Banking/finance (B/F)
Applications
#4806
System i hardware feature code
IBM 4764 PCI-X Cryptographic CoprocessorIBM Common Name
The 4764 Cryptographic Coprocessor provides both cryptographic coprocessor and secure-key
cryptographic accelerator functions in a single PCI-X card. The coprocessor functions are targeted to
banking and finance applications. The secure-key accelerator functions are targeted to improving the
performance of SSL (secure socket layer) and TLS (transport layer security) based transactions. The 4764
Cryptographic Coprocessor supports secure storage of cryptographic keys in a tamper-resistant module,
IBM i 6.1 Performance Capabilities Reference - January/April/October 2008
© Copyright IBM Corp. 2008 Chapter 8 Cryptography Performance 145


















