USER’S GUIDE
050396 65/173
66
This code allows the reset of the Watchdog Timer:
MOV 0C7H,#0AAH ; 1st TA Value
MOV 0C7H,#055H ; 2nd TA Value 2 Cycles
SETB IP.7 ; Reset Watchdog Timer 1 Cycle
The Watchdog Timer bit may have been set using ORL IP, #80H which
takes two cycles.
This code allows the reset of the Watchdog Timer using a different ap-
proach:
MOV A, #55H ; Setup Acc for fast write
MOV 0C7H, #0AAH ; 1st TA Value
MOV 0C7H, A ; 2nd TA Value 1 Cycle
MOV A, IP ; Get Current IP 1 Cycle
ORL A, #80H ; Prepare for fast write 1 Cycle
MOV IP, A ; Reset Watchdog Timer 1 Cycle
Note that a new value for IP could have been retrieved from any direct
register instead of the current IP.
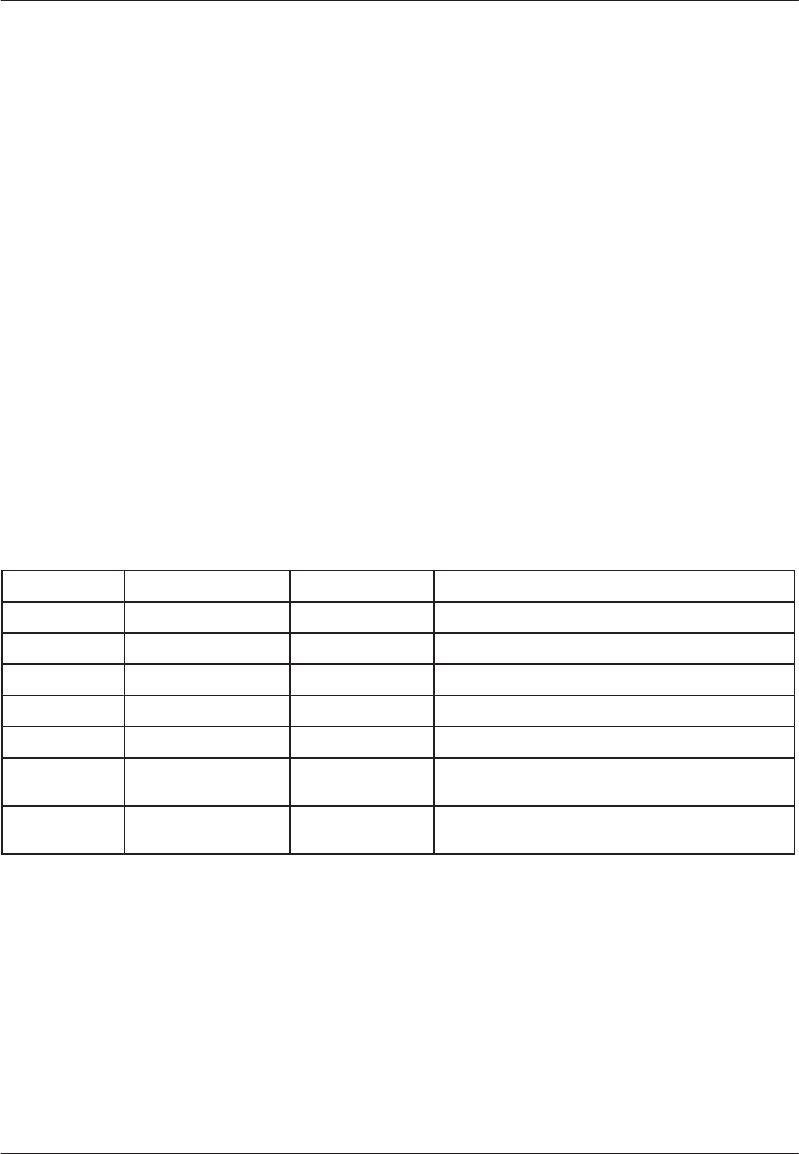
The bits which are write access–protected by the Timed Access function are listed in Table 8–1.
TIMED ACCESS PROTECTED CONTROL BITS Table 8–1
BIT NAME MICRO VERSION LOCATION DESCRIPTION
EWT All Secure Micro PCON.2 Enables the Watchdog Timer Reset function
RWT All Secure Micro IP.7 Resets the Watchdog Timer count
STOP All Secure Micro PCON.1 Stop Mode Enable
POR All Secure Micro PCON.6 Power On Reset
PAA DS5000 series MCON.1 Partition Address Access bit (protects PA3–0)
PA3–0 DS5001, DS5002
series
MCON.7–4 Partition Address bits
AE DS5001, DS5002
series
RPCTL.4 Access Enable
The Secure Microcontroller family has a variety of con-
trol bits that are critical to the correct operation of the
processor. Several of these are nonvolatile and will not
be altered by a reset. Thus they must be protected from
an accidental write by software that has gone out of con-
trol. This is a possibility in all microprocessor based sys-
tems, especially those in an industrial environment.
While the Watchdog Timer will recover from this condi-
tion, the critical bits must be protected during the interval
before the time–out of the Watchdog Timer.
The Secure Microcontroller family actually has two lev-
els of protection for these critical bits. The most critical
SFR bits can only be altered using the Bootstrap Load-
er. An example is the Range function that determines
the total memory. There is no need for an application to
modify this bit during normal operation. For those critical
bits that might need to be modified during normal opera-
tion, the Timed Access procedure protects against an
inadvertent write operation.


















