TANDBERG Gatekeeper User Guide
Page 49 of 105
11.3. Dialing Public IP Addresses
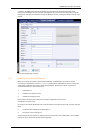
Figure 22: Dialing a public IP address
Figure 22 shows a private endpoint (1001) calling an endpoint on a public IP address. In this case the
public endpoint is not registered to a Gatekeeper and can only be reached using its IP address. In order
to successfully traverse the firewall it is necessary for the call to be relayed through the Border
Controller; the TANDBERG Gatekeeper should not attempt to place the call directly to the public
endpoint.
In order to achieve this:
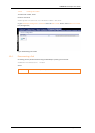
1. On the Gatekeeper, set Calls to unknown IP addresses to Indirect. This can be done via either:
xconfiguration Gatekeeper CallsToUnknownIPAddresses: Indirect
or Gatekeeper Configuration -> Gatekeeper and in the Configuration section, from the Calls to
unknown IP addresses drop-down menu selecting Indirect.
This setting will force the Gatekeeper to forward calls to any IP address it does not have locally
registered to the TANDBERG Border Controller, thereby allowing the Border Controller itself to
relay the call to the endpoint on the public IP address.
2. On the Border Controller, set Calls to unknown IP addresses to Direct.
This setting will allow the Border Controller to connect any call that it receives from the internal
Gatekeeper out to systems on the public Internet.
3. From Endpoint 1001, dial 213.228.193.162.
11.4. Neighbored Enterprises
If two enterprises have deployed Border Controllers for firewall traversal, the two Border Controllers may
be neighbored to allow calls to be placed from one enterprise to another. Neighboring will reduce call
setup time compared to URI dialing (see URI Dialing, section 9). The disadvantage of neighboring is that
the Border Controllers have to be configured with each other's addresses before the call can be made.
Each Gatekeeper and its matching Border Controller are neighbored as described in section 11.1.
Border Controllers A and B are then neighbored together.