SmartSwitch Router User Reference Manual 257
Chapter 17: Access Control List Configuration Guide
that allow you to restrict traffic for a specific IP-based protocol; for example, the
acl permit|deny tcp command lets you restrict only TCP traffic. These variants
have the same syntax and fields as the acl permit|deny ip command.
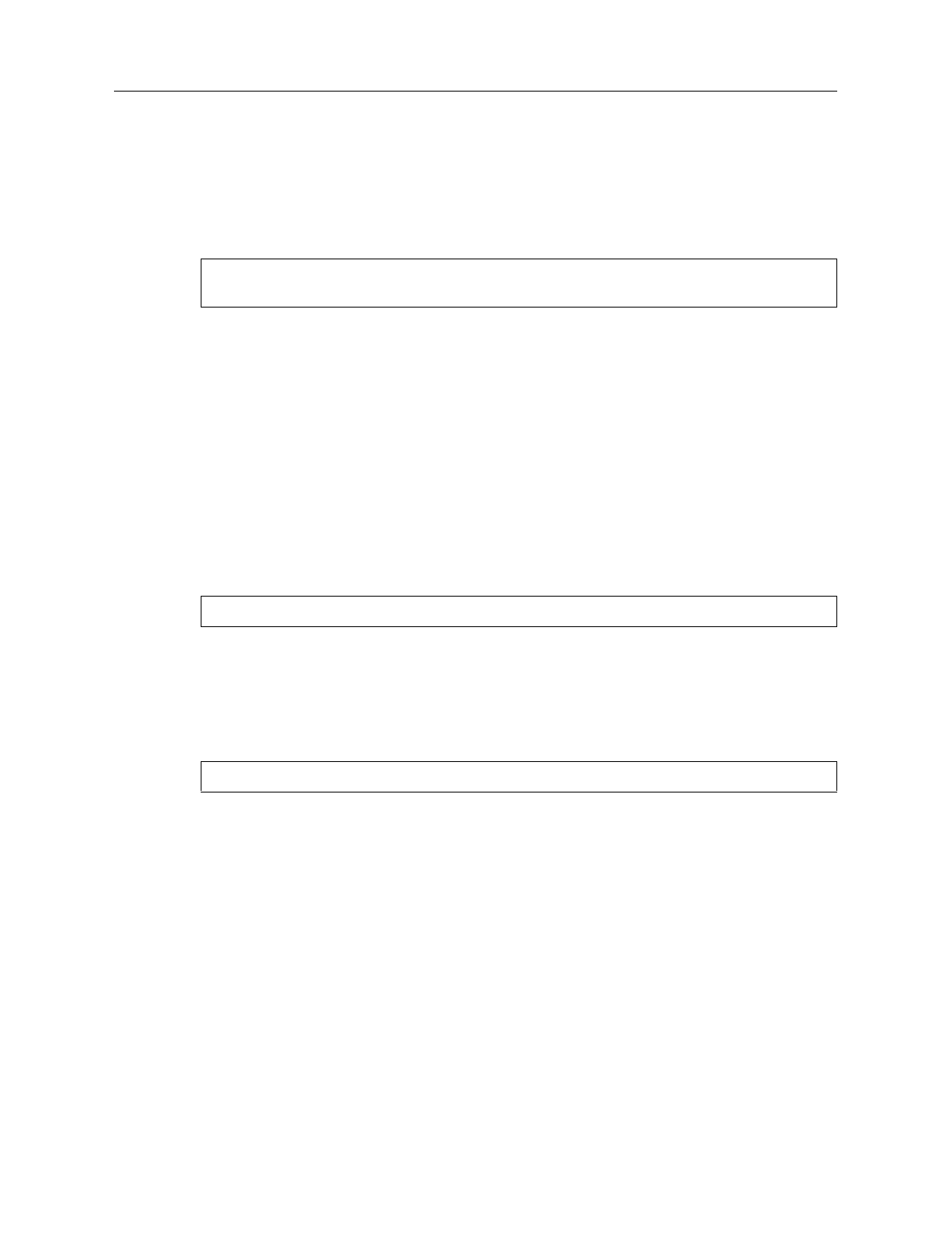
The following syntax description shows the fields of an IPX ACL rule:
Each field in an ACL rule is position sensitive. For example, for a rule for TCP traffic, the
source address must be followed by the destination address, followed by the source
socket and the destination socket, and so on.
Not all fields of an ACL rule need to be specified. If a particular field is not specified, it is
treated as a wildcard or “don't care” condition. However, if a field is specified, that
particular field will be matched against the packet. Each protocol can have a number of
different fields to match. For example, a rule for TCP can use socket port numbers, while a
rule for IPX can use a network node address.
Since each field is position sensitive, it may be necessary to “skip” some fields in order to
specify a value for another field. To skip a field, use the keyword any. For example, the
following ACL rule denies SMTP traffic between any two hosts:
Note that in the above example, the <tos> (Type of Service) field is not specified and is
treated as a wildcard. The any keyword is needed only to skip a wildcard field in order to
explicitly specify another field that is further down in the rule. If there are no other fields
to specify, the any keyword is not necessary. For example, the following ACL permits all
IP traffic to go through:
How ACL Rules are Evaluated
For an ACL with multiple rules, the ordering of the rules is important. When the SSR
checks a packet against an ACL, it goes through each rule in the ACL sequentially. If a
packet matches a rule, it is forwarded or dropped based on the permit or deny keyword
in the rule. All subsequent rules are ignored. That is, a first-match algorithm is used. There
is no hidden or implied ordering of ACL rules, nor is there precedence attached to each
field. The SSR simply goes down the list, one rule at a time, until there is a match.
Consequently, rules that are more specific (that is, with more selection criteria) should
acl <name> permit|deny ipx <SrcAddr> <SrcSocket> <DstAddr> <DstSocket>
<SrcNetMask> <DstNetMask>
acl nosmtp deny tcp any any smtp smtp
acl yesip permit ip


















