10-23
User Guide for Cisco Secure ACS for Windows Server
78-16592-01
Chapter 10 System Configuration: Authentication and Certificates
About Certification and EAP Protocols
The Database Replication log on the primary Cisco Secure ACS records
replication of master keys. Entries related to master key replication contain the
text “MKEYReplicate”.
The EAP-FAST master server setting has a significant effect upon EAP-FAST
authentication and replication, as follows:
• Enabled—When the EAP-FAST master server check box is selected, the
“Actual EAP-FAST server status” is
Master and Cisco Secure ACS ignores
the EAP-FAST settings, Authority ID, and master keys it receives from a
primary Cisco Secure ACS during replication, preferring instead to use
master keys it generates, its unique Authority ID, and the EAP-FAST settings
configured in its HTML interface.
Enabling the EAP-FAST master server setting requires providing for the
end-user client a PAC from the primary Cisco Secure ACS that is different
than the PAC from the secondary Cisco Secure ACS. Because the primary and
secondary Cisco Secure ACSes send different Authority IDs at the beginning
of the EAP-FAST transaction, the end-user client must have a PAC for each
Authority ID. A PAC generated by the primary Cisco Secure ACS is not
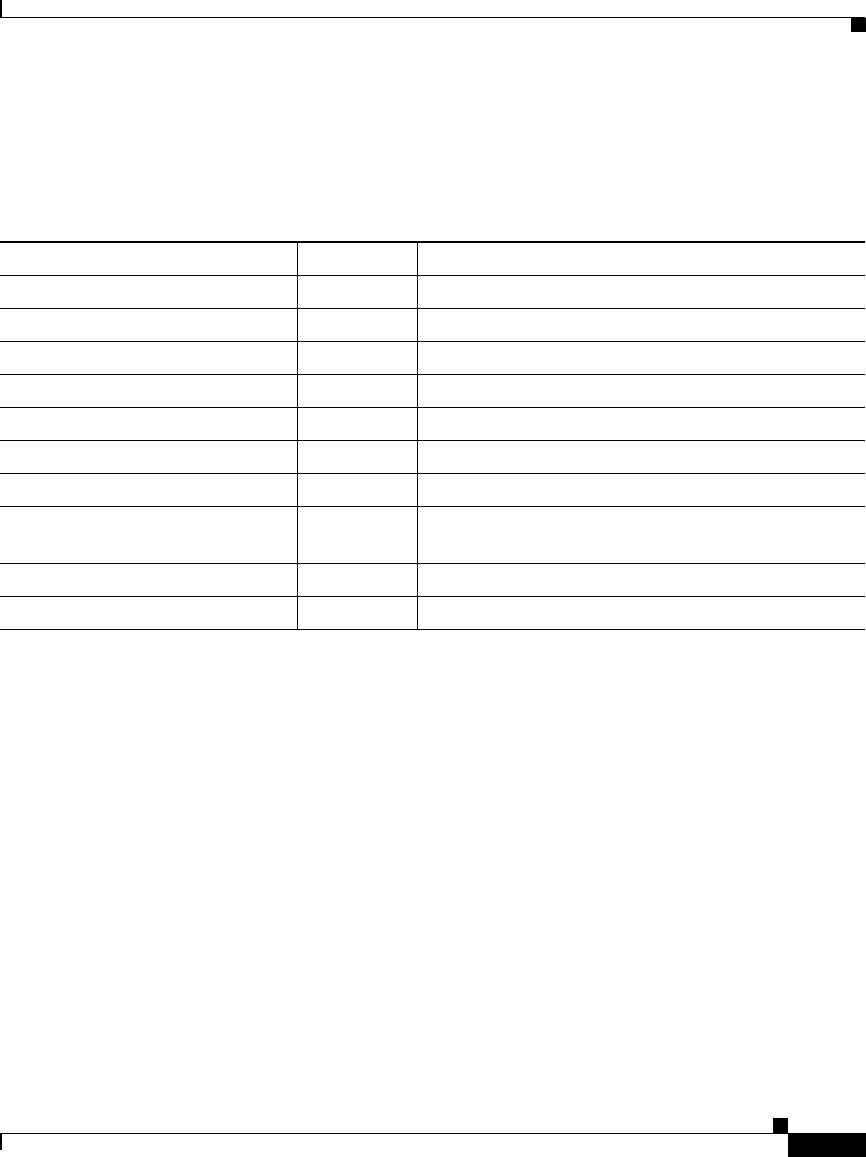
Table 10-2 EAP-FAST Components and Replication
EAP-FAST Component Replicated? Configurable?
EAP-FAST Enable No Yes, on the Global Authentication Setup page.
Master key TTL Yes Yes, on the Global Authentication Setup page.
Retired master key TTL Yes Yes, on the Global Authentication Setup page.
PAC TTL Yes Yes, on the Global Authentication Setup page.
Authority ID Yes No, generated by Cisco Secure ACS.
Authority ID info Yes Yes, on the Global Authentication Setup page.
Client initial message Yes Yes, on the Global Authentication Setup page.
Master keys Yes No, generated by Cisco Secure ACS when TTL
settings dictate.
EAP-FAST master server No Yes, on the Global Authentication Setup page.
Actual EAP-FAST server status No No, determined by Cisco Secure ACS.


















