Security: 802.1X Authentication
Authenticator Overview
390 Cisco Small Business 200, 300 and 500 Series Managed Switch Administration Guide (Internal Version)
19
NOTE
• When web-based authentication is not supported, guest VLAN and DVA
cannot be configured in multi-session mode.
• When web-based authentication is supported, guest VLAN and DVA can be
configured in multi-session mode
Unauthenticated VLANs and the Guest VLAN
Unauthenticated VLANs and the guest VLAN provide access to services that do
not require the subscribing devices or ports to be 802.1X or MAC-Based
authenticated and authorized.
The guest VLAN is the VLAN that is assigned to an unauthorized client. You can
configure the guest VLAN and one or more VLANs to be unauthenticated in the
Security > 802.1X/MAC/Web Authentication > Properties page.
An unauthenticated VLAN is a VLAN that allows access by both authorized and
unauthorized devices or ports.
An unauthenticated VLAN has the following characteristics:
• It must be a static VLAN, and cannot be the guest VLAN or the default VLAN.
• The member ports must be manually configured as tagged members.
• The member ports must be trunk and/or general ports. An access port
cannot be member of an unauthenticated VLAN.
The guest VLAN, if configured, is a static VLAN with the following characteristics:
• It must be manually defined from an existing static VLAN.
• The guest VLAN cannot be used as the Voice VLAN or an unauthenticated
VLAN.
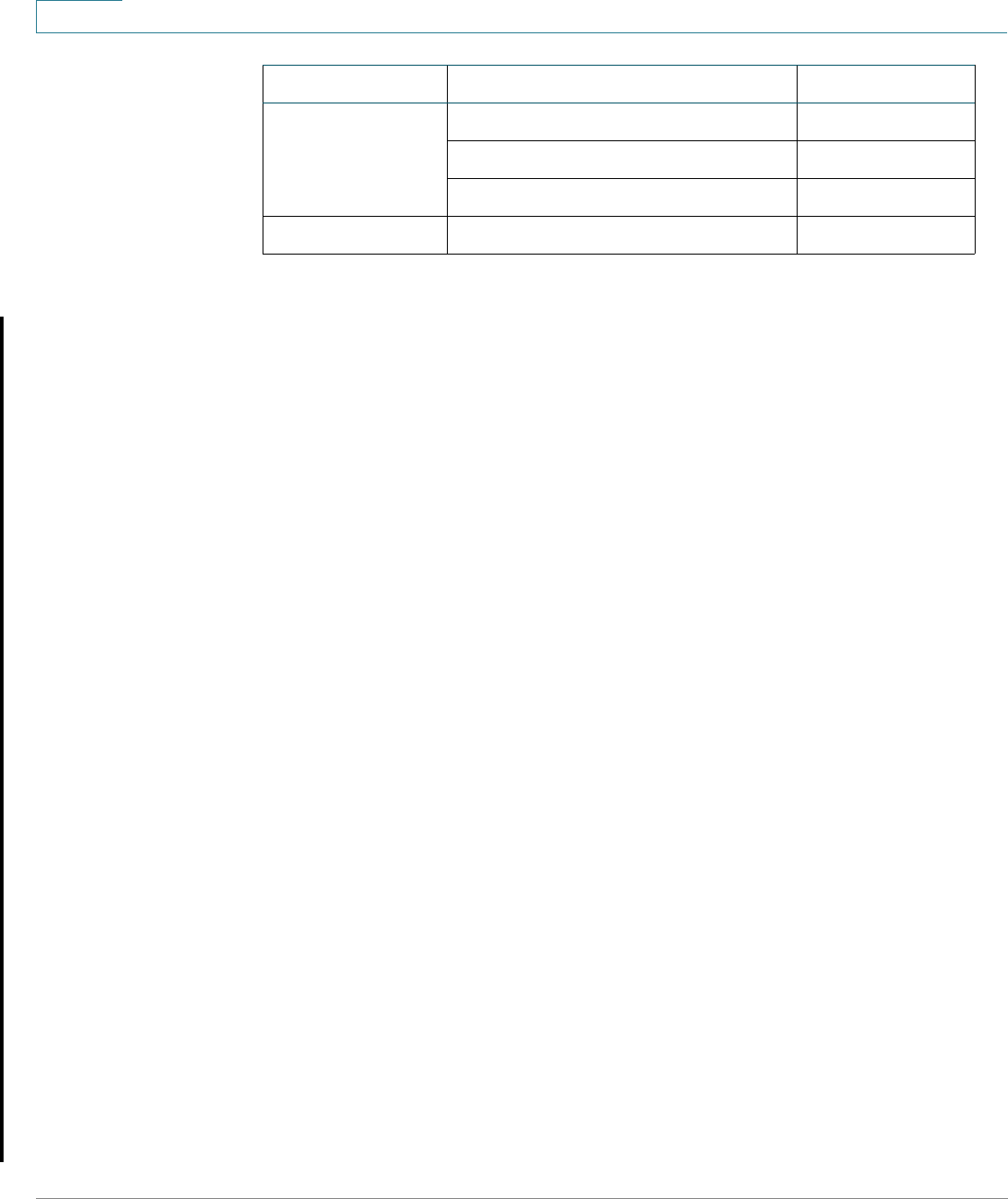
See “Table 3 Guest VLAN Support and RADIUS-VLAN Assignment Support” to
see a summary of the modes in which guest VLAN is supported.
SG500X Native Ye s
Basic Hybrid - Layer 2 Yes
Basic Hybrid - Layer 3 No
SG500XG Same as Sx500 Ye s
SKU System Mode WBA Supported


















