xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
centralized and distributed network management strategies. It includes improvements in the
Structure of Management Information (SMI) and adds some security features.
SNMPv3 - Specifies that the SNMP version 3 will be used. SNMPv3 provides secure access
to devices through a combination of authentication and encrypting packets over the network.
Security Level
The Security Level settings only apply to SNMPv3.
NoAuthNoPriv - Specifies that there will be no authorization and no encryption of packets sent
between the Switch and a remote SNMP manager.
AuthNoPriv - Specifies that authorization will be required, but there will be no encryption of
packets sent between the Switch and a remote SNMP manager.
AuthPriv - Specifies that authorization will be required, and that packets sent between the
Switch and a remote SNMP manger will be encrypted.
To implement the new settings, click Apply.
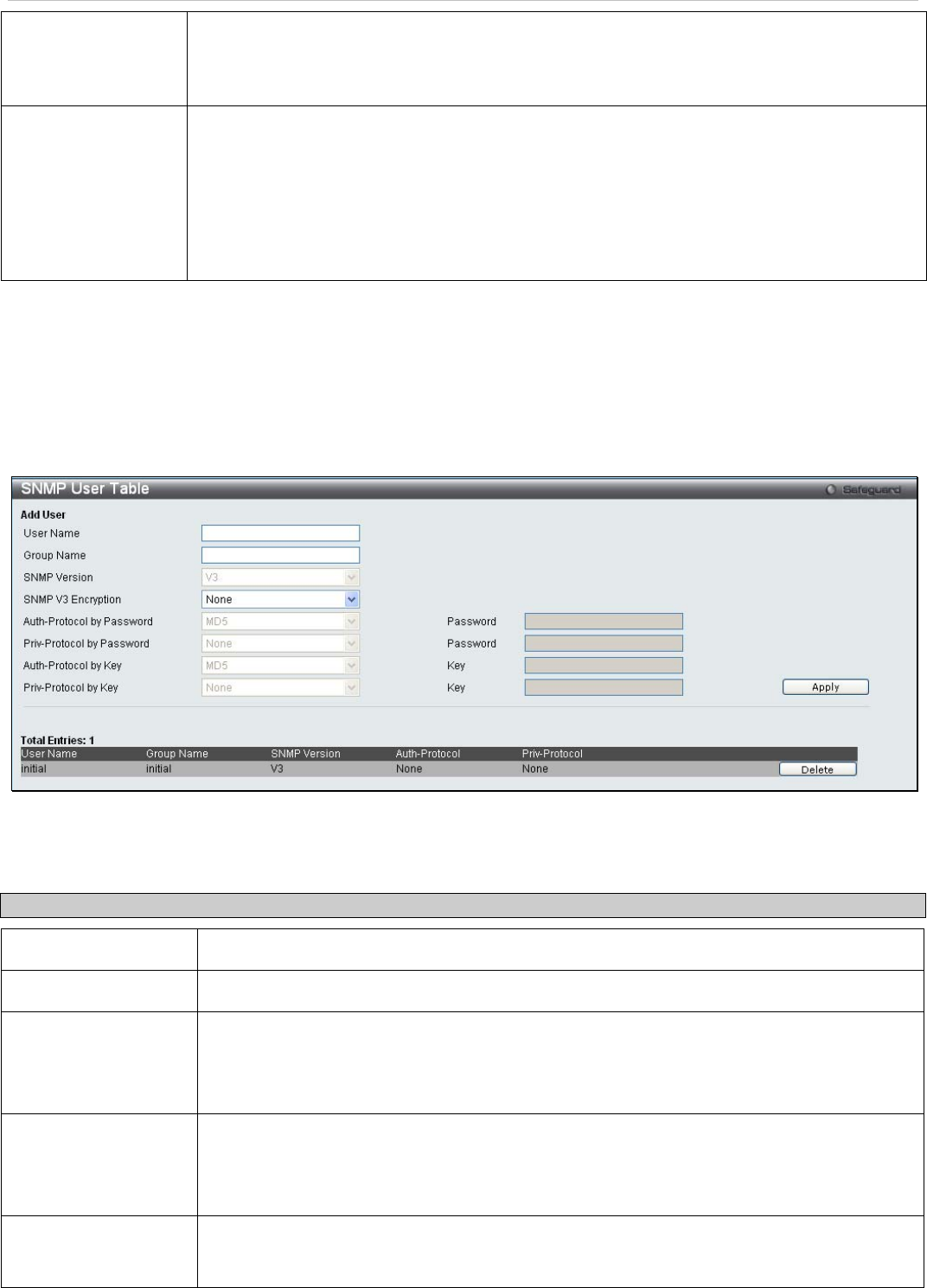
SNMP User Table
This window displays all of the SNMP User's currently configured on the Switch and also allows you to add new users.
To view this window, click Configuration > SNMP Settings > SNMP User Table:
Figure 2 - 34. SNMP User Table window
To delete an existing SNMP User Table entry, click the corresponding Delete button.
The following parameters may be set:
Parameter Description
User Name
An alphanumeric string of up to 32 characters. This is used to identify the SNMP users.
Group Name
This name is used to specify the SNMP group created can request SNMP messages.
SNMP Version
V1 - Indicates that SNMP version 1 is in use.
V2 - Indicates that SNMP version 2 is in use.
V3 - Indicates that SNMP version 3 is in use.
SNMP V3 Encryption
None – Indicates that there is no SNMP V3 Encryption
Password – Indicates that there is SNMP V3 Encryption through a password
Key – Indicates that there is SNMP V3 Encryption through a key.
Auth-Protocol by
Password
MD5 - Indicates that the HMAC-MD5-96 authentication level will be used.
SHA - Indicates that the HMAC-SHA authentication protocol will be used.
40


















