48
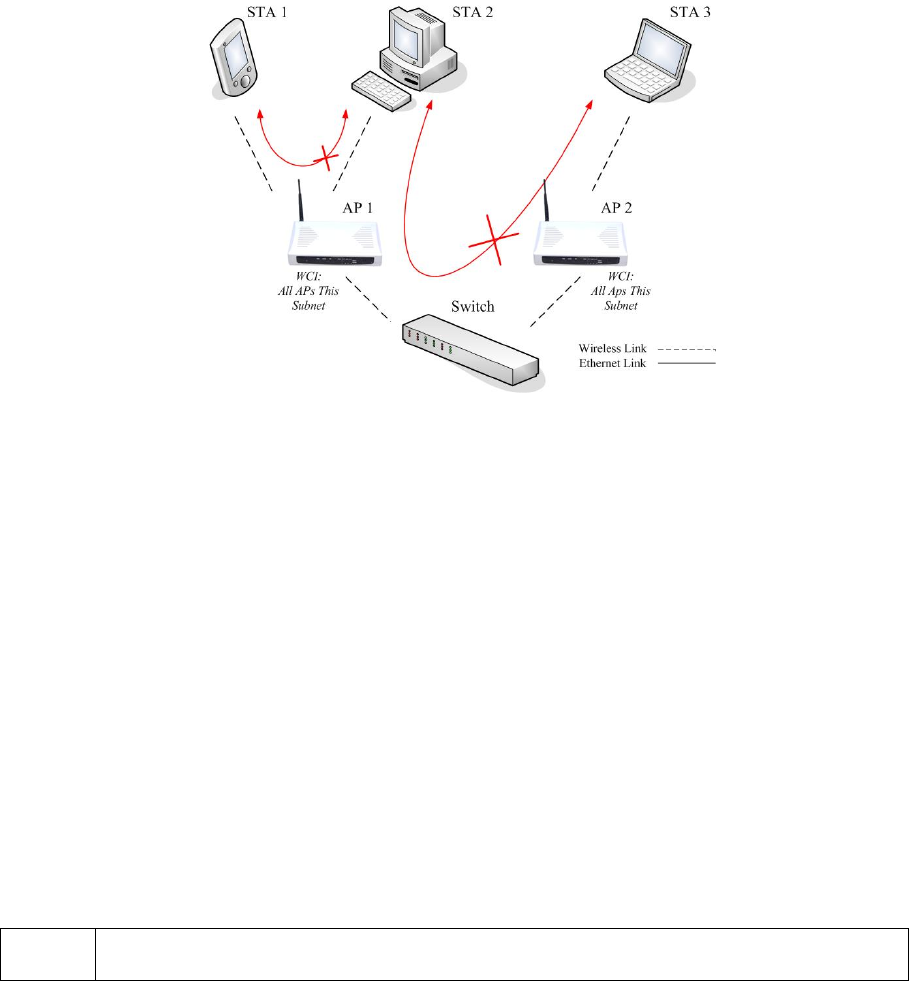
Fig. 76. Behavior of the “All APs on This Subnet” wireless client isolation option.
As illustrated in Fig. when AP 1 and AP 2 are using the “This AP Only” option, wireless traffic be-
tween STA 1 and STA 2 is blocked by AP 1, while wireless traffic between STA 2 and STA 3, which
are associated with different APs, is still allowed. If the “All APs in This Subnet” option is used as
shown in Fig. , AP 1 and AP 2 communicates with each other via an inter-AP protocol to share their
STA association information to block wireless traffic among all the STAs.
There are up to 7 security modes:
z Open System. No authentication, no data encryption.
z Static WEP. WEP (Wired Equivalent Privacy) keys must be manually configured.
z Static TKIP (WPA-PSK). Only TKIP (Temporal Key Integrity Protocol) mechanism of WPA
(Wi-Fi Protected Access) is enabled. In this mode, you have to specify the Pre-shared key,
which will be used by the TKIP engine as a master key to generate keys that actually encrypt
outgoing packets and decrypt incoming packets.
NOTE:
The number of characters of the Pre-shared key setting must be at least 8 and can be up
to 63.
z IEEE 802.1x EAP without Encryption (EAP-MD5). The IEEE 802.1x functionality is enabled
and the user-name/password-based EAP-MD5 authentication is used. No data encryption.
z IEEE 802.1x EAP with Static WEP (EAP-MD5). The IEEE 802.1x functionality is enabled
and the user-name/password-based EAP-MD5 authentication is used. Data encryption is
achieved by static WEP.
z IEEE 802.1x EAP with Dynamic WEP (EAP-TLS, EAP-TTLS, PEAP). The IEEE 802.1x
functionality is enabled and dynamic WEP key distribution authentication (EAP-TLS,
EAP-TTLS, or PEAP) is used. Data encryption is achieved by dynamic WEP.
z IEEE 802.1x EAP with Dynamic TKIP (WPA). This is a full WPA mode, in which both the
TKIP and IEEE 802.1x dynamic key exchange mechanisms are enabled. The IWE3200-H is
highly secured in this mode.


















