CHAPTER 7: ACCESS USING RADIUS ACCESS USING RADIUS
MULTILINK ML2400 ETHERNET COMMUNICATIONS SWITCH – INSTRUCTION MANUAL 7–3
10. If the supplicant does not have the necessary credentials, a RADIUS-Access-
Deny packet is relayed to the supplicant as an EAP-Failure frame. The access
to the network continues to be blocked.
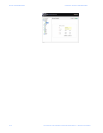
FIGURE 7–2: 802.1x authentication details
The ML2400 software implements the 802.1x authenticator. It fully conforms to the
standards as described in IEEE 802.1x, implementing all the state machines needed for
port-based authentication. The ML2400 software authenticator supports both EAPOL and
EAP over RADIUS to communicate to a standard 802.1x supplicant and RADIUS
authentication server.
The ML2400 software authenticator has the following characteristics:
• Allows control on ports using STP-based hardware functions. EAPOL frames are
Spanning Tree Protocol (STP) link Bridge PDUs (BPDU) with its own bridge multicast
address.
• Relays MD5 challenge (although not limited to) authentication protocol to RADIUS
server
• Limits the authentication of a single host per port
• The MultiLink switch provides the IEEE 802.1x MIB for SNMP management
754715A1.CDR
802.1x switch
u
Port Connected
Access Blocked
EAP Request Id
v
w
RADIUS Access Request
x
RADIUS Access Challenge
{
RADIUS Access Request
RADIUS Access Accept
|
Access Allowed
EAPOL EAP over RADIUS
EAP Request
y
EAP Response
z
EAP Success
}