29Planning the installation
What to do after installation
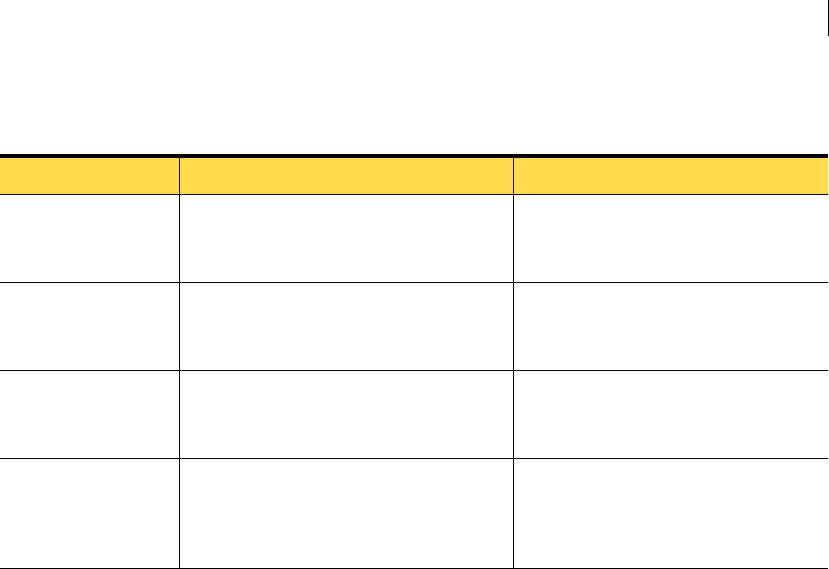
Table 2-5 lists the management server log files.
What to do after installation
You can begin enforcing the Symantec Critical System Protection policies on
agents immediately after agent installation and registration with the
management server.
Symantec recommends that you first apply a policy to a few agents, and then
verify that the agent computers are functioning properly with the applied
policy.
See the Symantec Critical System Protection Administration Guide for
information about applying policies to agents.
Table 2-5 Management server log files
File name Description Default location
sis-agent.*.log This log file is used for agent activity.
The asterisk in the file name represents a
version number.
Windows:
Program Files\Symantec\Critical System
Protection\Server\Tomcat\logs
sis-alert.*.log This log file is used for alert activity.
The asterisk in the file name represents a
version number.
Windows:
Program Files\Symantec\Critical System
Protection\Server\Tomcat\logs
sis-console.*.log This log file is used for console activity.
The asterisk in the file name represents a
version number.
Windows:
Program Files\Symantec\Critical System
Protection\Server\Tomcat\logs
sis-server.*.log This log file is used for general server
messages.
The asterisk in the file name represents a
version number.
Windows:
Program Files\Symantec\Critical System
Protection\Server\Tomcat\logs


















