42
S
S
C
C
A
A
N
N
F
F
O
O
R
R
S
S
I
I
T
T
E
E
S
S
U
U
R
R
V
V
E
E
Y
Y
(
(
O
O
N
N
L
L
Y
Y
F
F
O
O
R
R
C
C
L
L
I
I
E
E
N
N
T
T
M
M
O
O
D
D
E
E
A
A
N
N
D
D
W
W
I
I
R
R
E
E
L
L
E
E
S
S
S
S
R
R
O
O
U
U
T
T
I
I
N
N
G
G
C
C
L
L
I
I
E
E
N
N
T
T
M
M
O
O
D
D
E
E
)
)
S
S
t
t
e
e
p
p
1
1
:
:
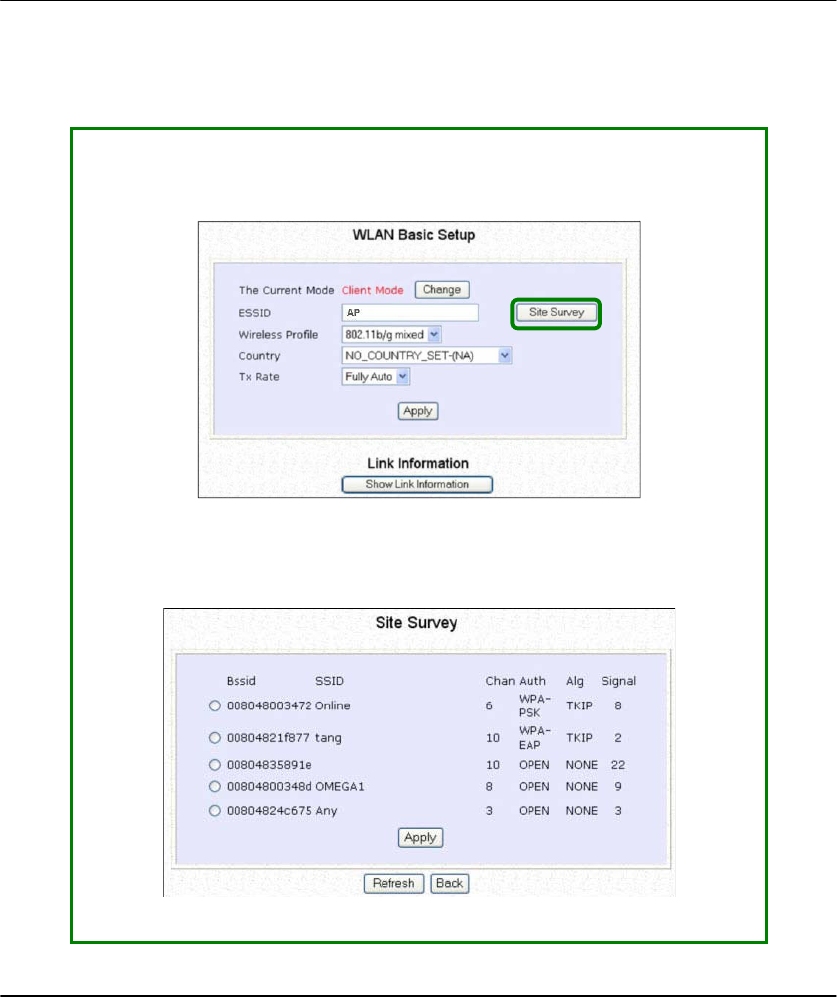
In the
M
M
o
o
d
d
e
e
S
S
e
e
t
t
u
u
p
p page, click on the
S
S
i
i
t
t
e
e
S
S
u
u
r
r
v
v
e
e
y
y button.
The
S
S
i
i
t
t
e
e
S
S
u
u
r
r
v
v
e
e
y
y provides a list of the
M
M
A
A
C
C
a
a
d
d
d
d
r
r
e
e
s
s
s
s
e
e
s
s
(
(
B
B
S
S
S
S
I
I
D
D
)
) and
S
S
S
S
I
I
D
D of
neighbouring access points detected, the
C
C
h
h
a
a
n
n (channels),
A
A
u
u
t
t
h
h
(Authentication),
A
A
l
l
g
g (Algorithm) used, and the strength of the
S
S
i
i
g
g
n
n
a
a
l
l
received.


















