73
S
S
E
E
C
C
U
U
R
R
E
E
S
S
H
H
E
E
L
L
L
L
H
H
O
O
S
S
T
T
C
C
O
O
M
M
M
M
A
A
N
N
D
D
L
L
I
I
N
N
E
E
I
I
N
N
T
T
E
E
R
R
F
F
A
A
C
C
E
E
SSH CLI (Secure Shell Host Command Line Interface)
SSH is designed and created to provide the best security when
accessing another computer remotely. Not only does it encrypt the
session, it also provides better authentication facilities and features that
increase the security of other protocols. It can use different forms of
encryption and ciphers.
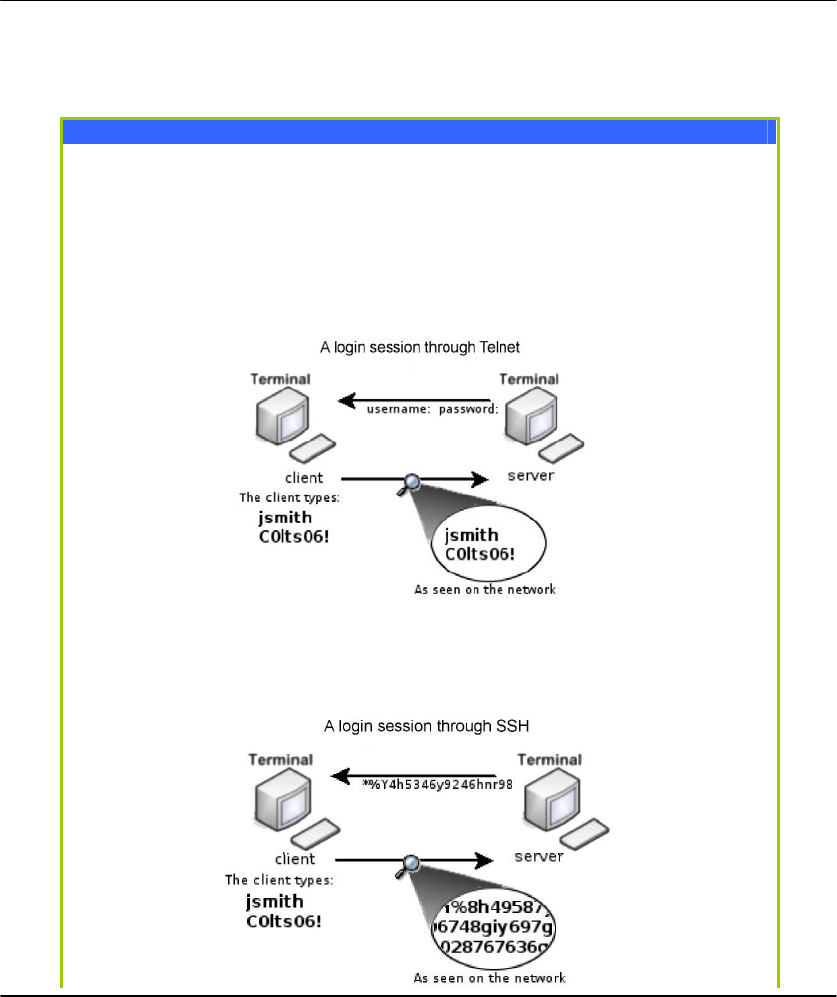
The first diagram below shows a telnet session.
The second diagram below shows how an encrypted connection like
SSH is not viewable on the network. The server still can read the
information, but only after negotiating the encrypted session with the
client.


















