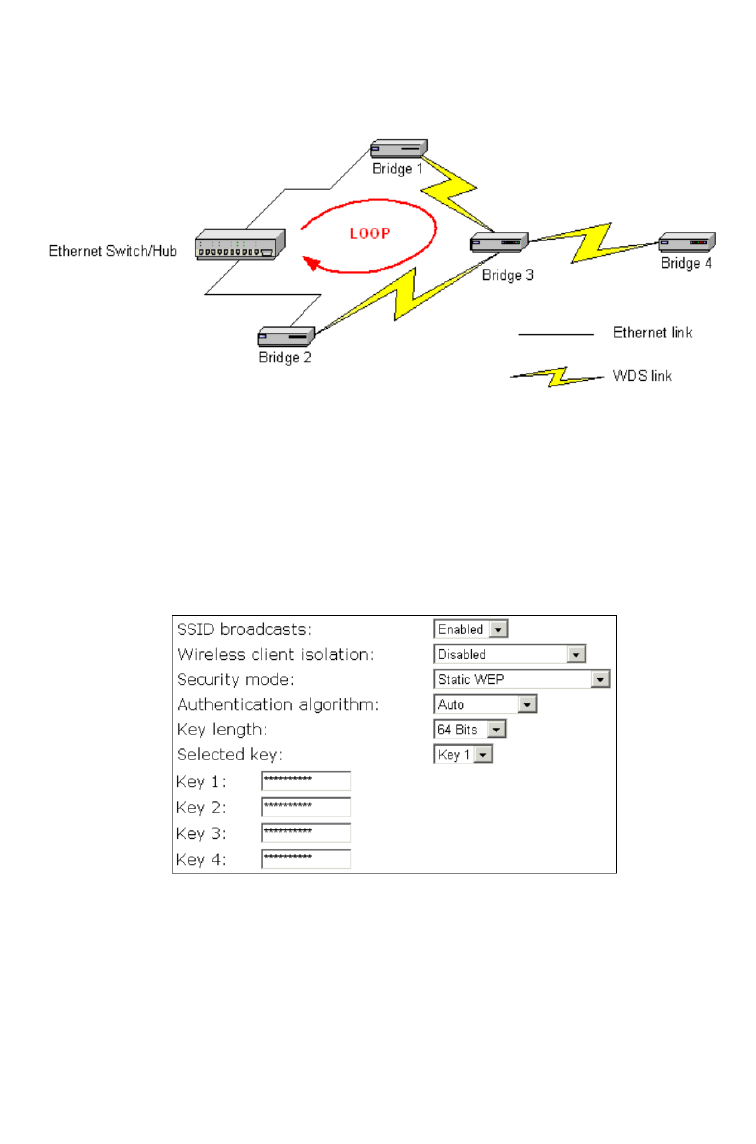
WARNING: Do not let your network topology consist of wireless bridges,
Ethernet switches, Ethernet links, and WDS links that form a loop. If there
are any loops that exist, packets will circle around the loops and network
performance will be seriously degraded.
Fig. 44 Network topology containing a loop.
Security
IEEE 802.11b/g security settings include SSID broadcasts, Security mode,
IEEE 802.11 Authentication algorithm, WEP keys, MAC-Address-Based
Access Control.
Basic
Fig. 45 Basic IEEE 802.11g security settings.
For security reasons, it’s highly recommended that the security mode be set
to options other than Open System. When the security mode is set to Open
System, no authentication or and data encryption will be performed.
Additionally, you can disable the SSID broadcasts func-tionality so that a
wireless client (STA or Bridge Slave) with an “ANY” SSID cannot associate
with the SMC2586W-G.
38


















