6-16
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 6 Configuring NAT (ASA 8.2 and Earlier)
Configuring NAT Control
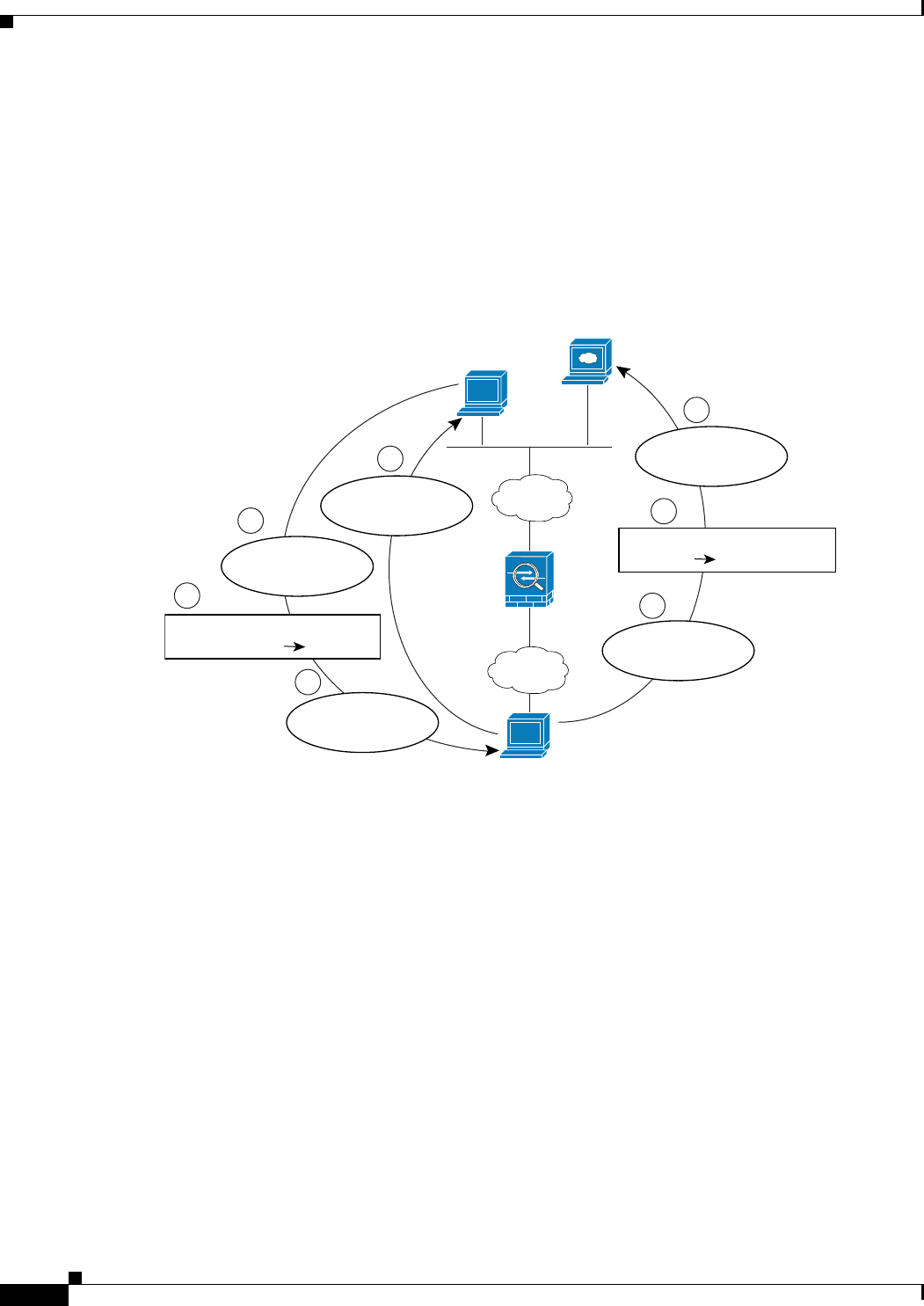
Figure 6-13 shows a web server and DNS server on the outside. The ASA has a static translation for the
outside server. In this case, when an inside user requests the address for ftp.cisco.com from the DNS
server, the DNS server responds with the real address, 209.165.20.10. Because you want inside users to
use the mapped address for ftp.cisco.com (10.1.2.56) you need to configure DNS reply modification for
the static translation.
Figure 6-13 DNS Reply Modification Using Outside NAT
Configuring NAT Control
NAT control requires that packets traversing from an inside interface to an outside interface match a NAT
rule. See the “NAT Control” section on page 6-4 for more information.
To enable NAT control, in the Configuration > Firewall > NAT Rules pane, check the Enable traffic
through the firewall without address translation check box.
ftp.cisco.com
209.165.201.10
DNS Server
Outside
Inside
User
10.1.2.27
Static Translation on Inside to:
10.1.2.56
130022
1
2
7
6
5
4
3
DNS Query
ftp.cisco.com?
DNS Reply
209.165.201.10
DNS Reply Modification
209.165.201.10 10.1.2.56
DNS Reply
10.1.2.56
FTP Request
209.165.201.10
Dest Addr. Translation
209.165.201.1010.1.2.56
FTP Request
10.1.2.56
Security
Appliance


















