11-17
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 11 Configuring Inspection of Basic Internet Protocols
FTP Inspection
load on the ASA. For example, if the DNS server is on the outside interface, you should enable DNS
inspection with snooping for all UDP DNS traffic on the outside interface. See the “Enabling DNS
Snooping” section on page 26-9.
Step 8 Click OK to return to the Protocol Inspections tab.
Step 9 Click OK to finish editing the service policy.
Step 10 Click Apply.
FTP Inspection
This section describes the FTP inspection engine. This section includes the following topics:
• FTP Inspection Overview, page 11-17
• Using Strict FTP, page 11-17
• Select FTP Map, page 11-18
• FTP Class Map, page 11-19
• Add/Edit FTP Traffic Class Map, page 11-19
• Add/Edit FTP Match Criterion, page 11-20
• FTP Inspect Map, page 11-21
FTP Inspection Overview
The FTP application inspection inspects the FTP sessions and performs four tasks:
• Prepares dynamic secondary data connection
• Tracks the FTP command-response sequence
• Generates an audit trail
• Translates the embedded IP address
FTP application inspection prepares secondary channels for FTP data transfer. Ports for these channels
are negotiated through PORT or PASV commands. The channels are allocated in response to a file
upload, a file download, or a directory listing event.
Note If you disable FTP inspection engines with the no inspect ftp command, outbound users can start
connections only in passive mode, and all inbound FTP is disabled.
Using Strict FTP
Using strict FTP increases the security of protected networks by preventing web browsers from sending
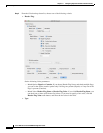
embedded commands in FTP requests. To enable strict FTP, click the Configure button next to FTP on
the Configuration > Firewall > Service Policy Rules > Edit Service Policy Rule > Rule Actions >
Protocol Inspection tab.
After you enable the strict option on an interface, FTP inspection enforces the following behavior: