30-4
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 30 Configuring the ASA CX Module
Information About the ASA CX Module
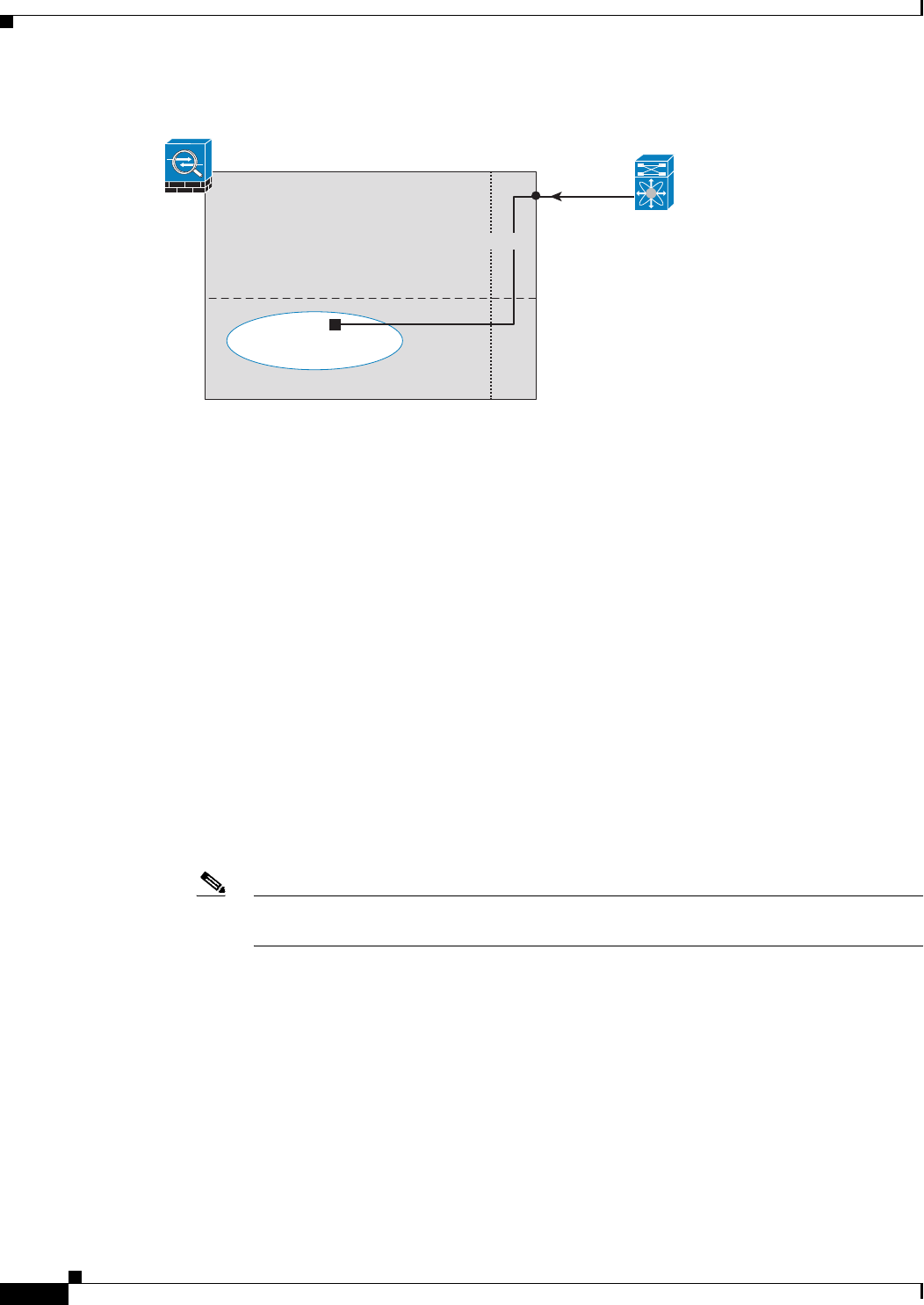
Figure 30-3 ASA CX Traffic-Forwarding
Information About ASA CX Management
• Initial Configuration, page 30-4
• Policy Configuration and Management, page 30-5
Initial Configuration
For initial configuration, you must use the CLI on the ASA CX module to run the setup command and
configure other optional settings.
To access the CLI, you can use the following methods:
• ASA 5585-X:
–
ASA CX console port—The ASA CX console port is a separate external console port.
–
ASA CX Management 1/0 interface using SSH—You can connect to the default IP address
(192.168.8.8), or you can use ASDM to change the management IP address and then connect
using SSH. The ASA CX management interface is a separate external Gigabit Ethernet
interface.
Note You cannot access the ASA CX hardware module CLI over the ASA backplane using the
session command.
• ASA 5512-X through ASA 5555-X:
–
ASA session over the backplane—If you have CLI access to the ASA, then you can session to
the module and access the module CLI.
–
ASA CX Management 0/0 interface using SSH—You can connect to the default IP address
(192.168.1.2), or you can use ASDM to change the management IP address and then connect
using SSH. These models run the ASA CX module as a software module. The ASA CX
management interface shares the Management 0/0 interface with the ASA. Separate MAC
addresses and IP addresses are supported for the ASA and ASA CX module. You must perform
configuration of the ASA CX IP address within the ASA CX operating system (using the CLI
Gig 0/3
SPAN
Port
ASA
Main System
ASA CX
Backplane
ASA CX inspection
Forwarded Traffic
Switch
303699


















