25-17
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 25 Configuring the ASA for Cisco Cloud Web Security
Configuring Cisco Cloud Web Security
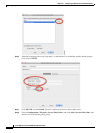
Step 10 Click Apply.
Examples
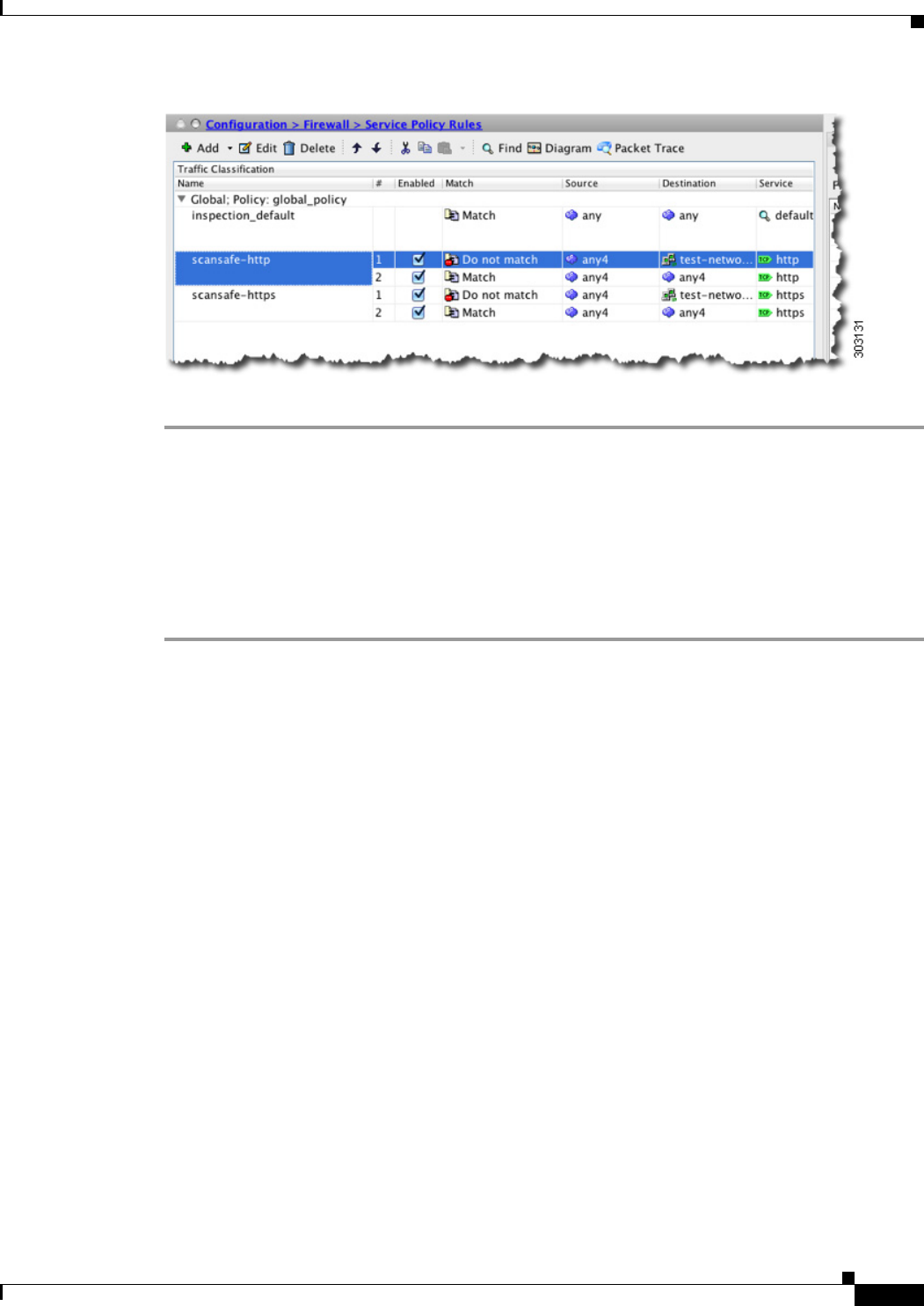
The following example exempts all IPv4 HTTP and HTTPS traffic going to the 10.6.6.0/24
(test_network), and sends all other HTTPS and HTTPS traffic to Cloud Web Security, and applies this
service policy rule to all interfaces as part of the existing global policy. If the Cloud Web Security server
is unreachable, the ASA drops all matching traffic (fail close). If a user is not have user identity
information, the default user Boulder and group Cisco is used.
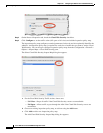
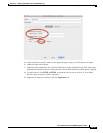
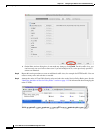
Step 1 Choose Configuration > Firewall > Service Policy Rules, and click Add > Service Policy Rule. Add
this rule to the default global_policy: