6-21
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 6 Configuring NAT (ASA 8.2 and Earlier)
Using Dynamic NAT
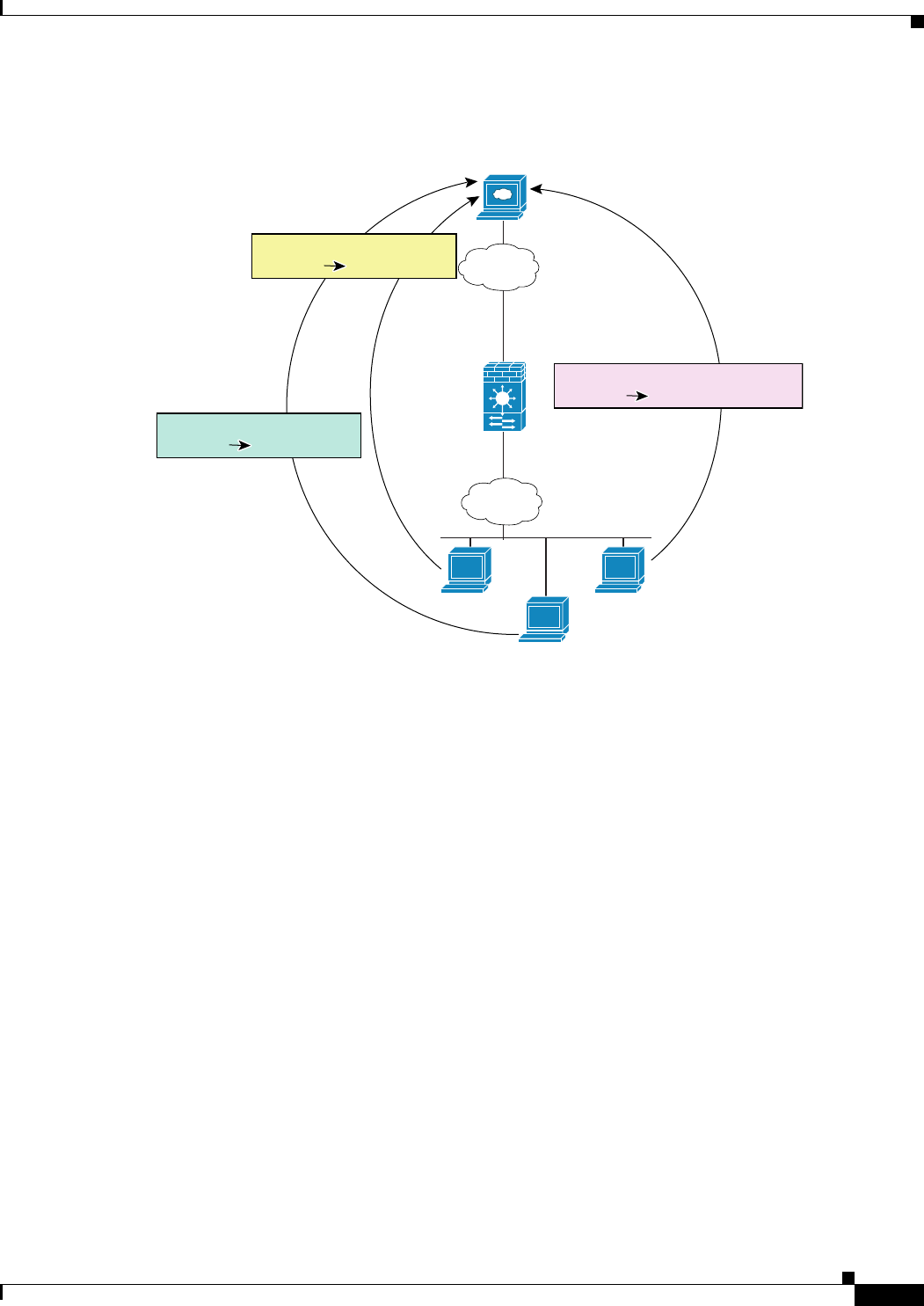
Figure 6-17 NAT and PAT Together
Outside NAT
If a NAT rule translates addresses from an outside interface to an inside interface, then the rule is an
outside NAT rule, and you need to specify that it translates inbound traffic. If you also want to translate
the same traffic when it accesses a lower security interface (for example, traffic on a DMZ is translated
when accessing the Inside and the Outside interfaces), then you can create a second NAT rule using the
same NAT ID (see Figure 6-18), but specifying outbound. Note that for outside NAT (DMZ interface to
Inside interface), the inside host uses a static rule to allow outside access, so both the source and
destination addresses are translated.
Web Server:
www.cisco.com
Outside
Inside
Global 1: 209.165.201.3-
209.165.201.4
Global 1: 209.165.201.5
NAT 1: 10.1.2.0/24
10.1.2.27
10.1.2.28
10.1.2.29
132928
Translation
209.165.201.310.1.2.27
Translation
209.165.201.410.1.2.28
Translation
209.165.201.5:609610.1.2.29


















