xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
Public Key Algorithm
HMAC-RSA Tick the check box to enable the HMAC (Hash for Message Authentication Code)
mechanism utilizing the RSA encryption algorithm. The default is enabled.
HMAC-DSA Tick the check box to enable the HMAC (Hash for Message Authentication Code)
mechanism utilizing the Digital Signature Algorithm encryption. The default is enabled.
Click Apply to implement changes made.
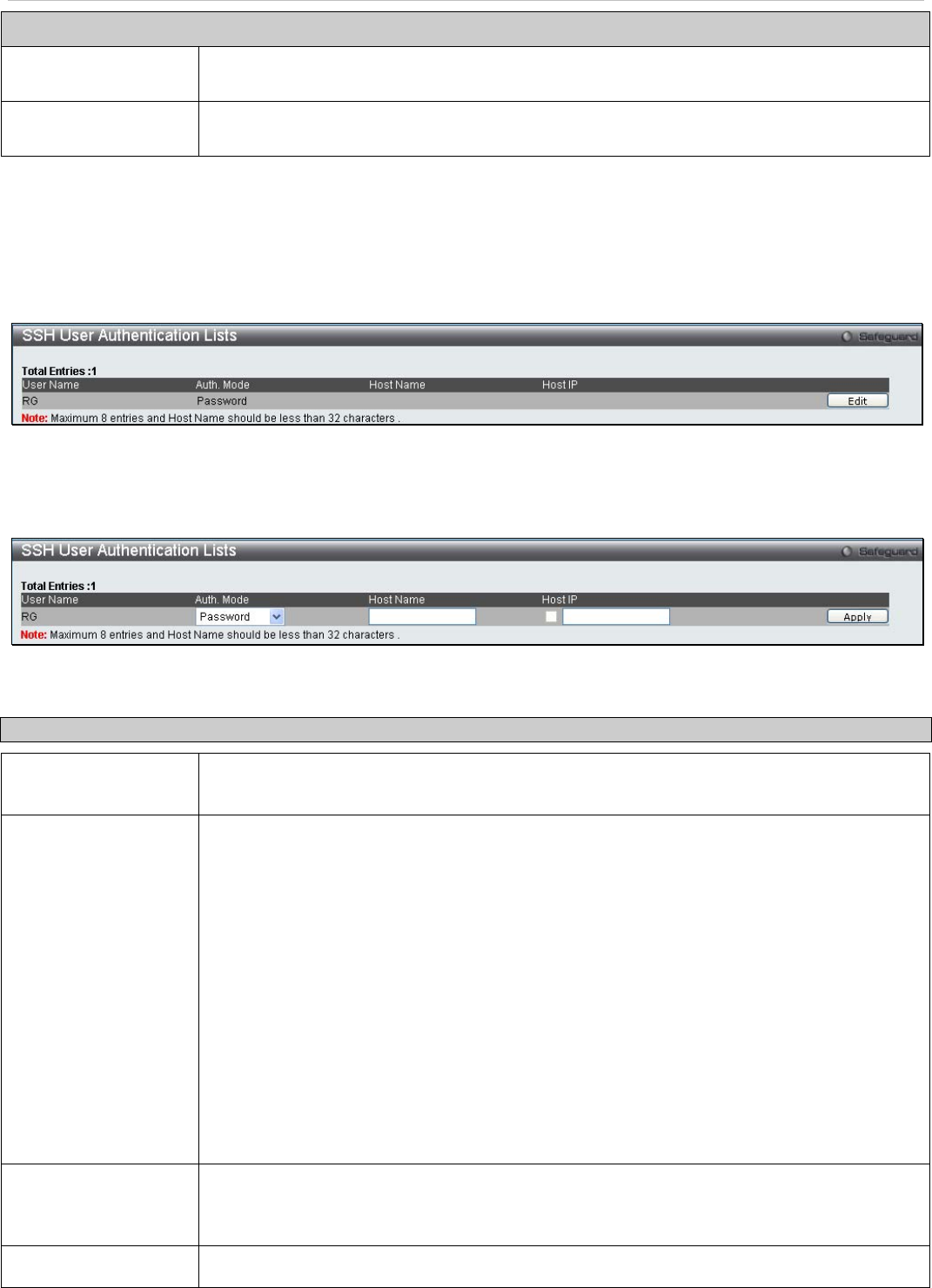
SSH User Authentication Lists
The following windows are used to configure parameters for users attempting to access the Switch through SSH.
To access the following window, click Security > SSH > SSH User Authentication Lists:
Figure 5 - 31. SSH User Authentication Lists window
In the example above, the User Account “RG” has been previously set using the User Accounts window in the
Configuration folder. A User Account MUST be set in order to set the parameters for the SSH user. To edit the
parameters for a SSH user, click on the corresponding Edit button, which will reveal the following window to configure:
Figure 5 - 32. SSH User Authentication Lists (Edit) window
The user may set the following parameters:
Parameter Description
User Name
Enter a User Name of no more than 15 characters to identify the SSH user. This User Name
must be a previously configured user account on the Switch.
Auth. Mode
The administrator may choose one of the following to set the authorization for users
attempting to access the Switch.
Host Based – This parameter should be chosen if the administrator wishes to use a remote
SSH server for authentication purposes. Choosing this parameter requires the user to input
the following information to identify the SSH user.
Host Name – Enter an alphanumeric string of no more than 32 characters to identify
the remote SSH user.
Host IP – Enter the corresponding IP address of the SSH user.
Password – This parameter should be chosen if the administrator wishes to use an
administrator-defined password for authentication. Upon entry of this parameter, the Switch
will prompt the administrator for a password, and then to re-type the password for
confirmation.
Public Key – This parameter should be chosen if the administrator wishes to use the
publickey on a SSH server for authentication.
Host Name
Enter an alphanumeric string of no more than 32 characters to identify the remote SSH user.
This parameter is only used in conjunction with the Host Based choice in the Auth. Mode
field.
Host IP
Enter the corresponding IP address of the SSH user. This parameter is only used in
138


















