xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
the device successfully through the RADIUS server or through the local method, 3 kinds of privilege levels can be
assigned to the user and the user can not use the “enable admin” command to promote to the admin privilege level.
NOTE: TACACS, XTACACS and TACACS+ are separate entities and are not
compatible. The Switch and the server must be configured exactly the same, using the
same protocol. (For example, if the Switch is set up for TACACS authentication, so must
be the host server.)
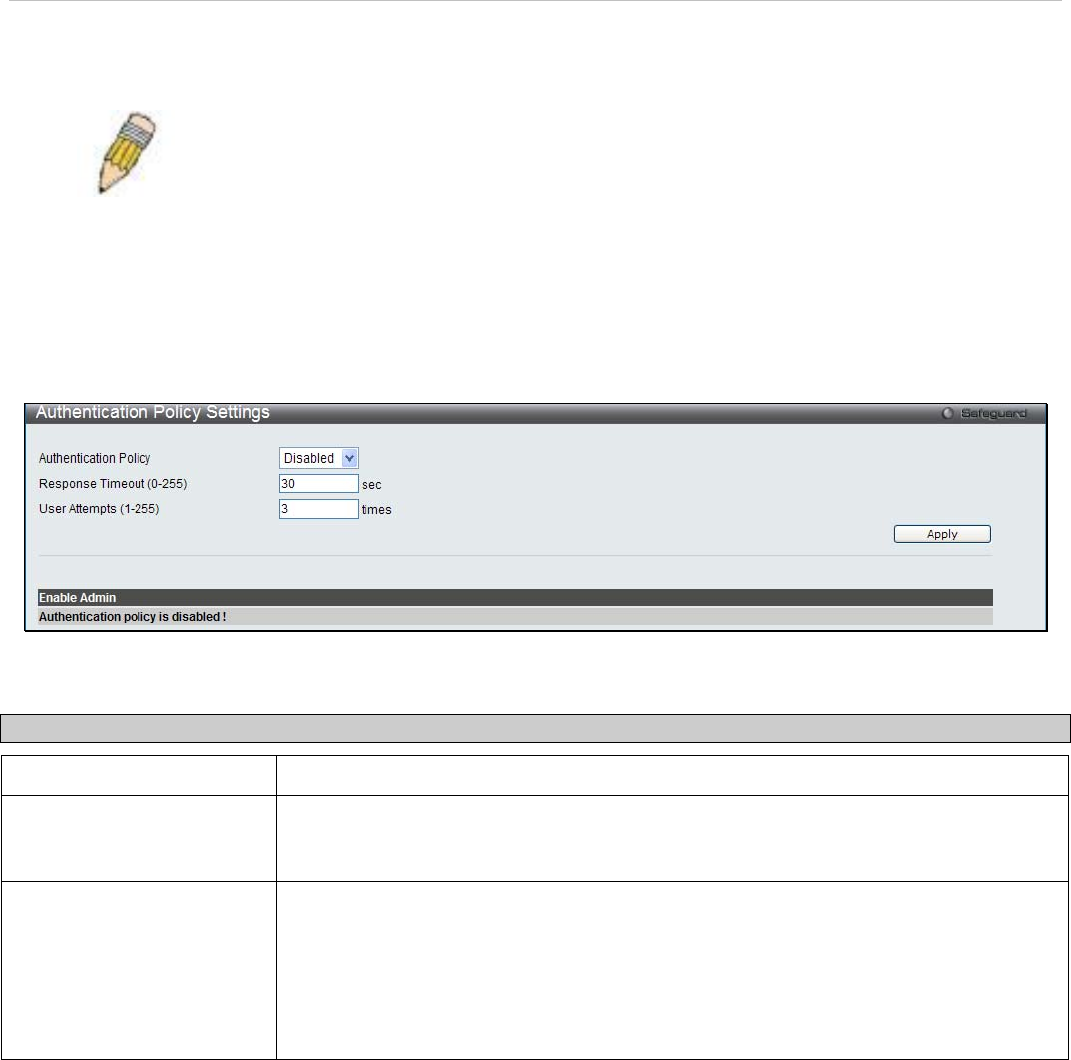
Authentication Policy Settings
This window offers an administrator-defined authentication policy for users trying to access the Switch. When Enabled,
the device will check the Login Method List and choose a technique for user authentication upon login.
To access the following window, click Security > Access Authentication Control > Authentication Policy Settings:
Figure 5 - 33. Authentication Policy Settings window
The following parameters can be set:
Parameters Description
Authentication Policy
Use the pull-down menu to enable or disable the Authentication Policy on the Switch.
Response Timeout (0-255) This field will set the time the Switch will wait for a response of authentication from the
user. The user may set a time between 0 and 255 seconds. The default setting is 30
seconds.
User Attempts (1-255) This command will configure the maximum number of times the Switch will accept
authentication attempts. Users failing to be authenticated after the set amount of
attempts will be denied access to the Switch and will be locked out of further
authentication attempts. Command line interface users will have to wait 60 seconds
before another authentication attempt. Telnet and web users will be disconnected from
the Switch. The user may set the number of attempts from 1 to 255. The default setting
is 3.
Click Apply to implement changes made.
Application Authentication Settings
This window is used to configure switch configuration applications (console, Telnet, SSH, web) for login at the user
level and at the administration level (Enable Admin) utilizing a previously configured method list.
To view the following window, click Security > Access Authentication Control > Application Authentication
Settings:
140


















