Copying Network Profiles to the Camera
Using the UT-1 with a Computer28
10
Enter the following information and click Next.
• Network name (SSID): Enter a network name or choose from a
list of existing networks. Do not change the name if it is
supplied automatically.
• Communication mode: Select Infrastructure or Ad-hoc.
• Channel: Select a channel (ad hoc only; in infrastructure
mode, the UT-1 will choose the channel automatically). Note
that if a matching SSID is detected on a different channel,
the UT-1 may change the channel automatically.
• Authentication: The authentication used on the network.
Choose from open system, shared key, WPA-PSK, and
WPA2-PSK (infrastructure) or from open system and shared
key (ad hoc).
• Encryption: The encryption used on the network. The options
available depend on the authentication used.
Open: None; 64- or 128-bit WEP
Shared: 64- or 128-bit WEP
WPA-PSK: TKIP; AES
WPA2-PSK: AES
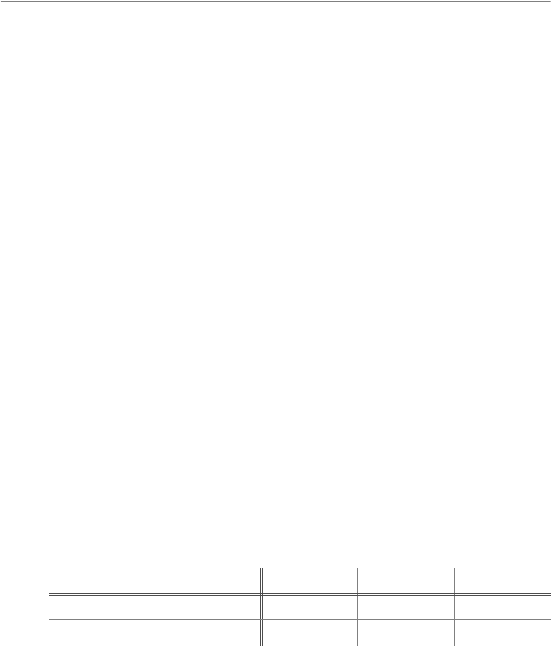
• Encryption key: If the network uses encryption, enter the
network key. The number of characters required depends
on the type of key used:
Note that depending on the device and the key setting used,
the UT-1 may fail to connect. If this occurs, try choosing a
different key setting.
• Key index: If WEP64 or WEP128 is selected for Encryption,
choose a key index (the default index is 1). A key index is not
required when None is selected.
WEP (64-bit) WEP (128-bit) TKIP, AES
Number of characters (ASCII) 5 13 8–63
Number of characters (hex) 10 26 64


















