P-334U/P-335U User’s Guide
140 Chapter 13 IPSec VPN
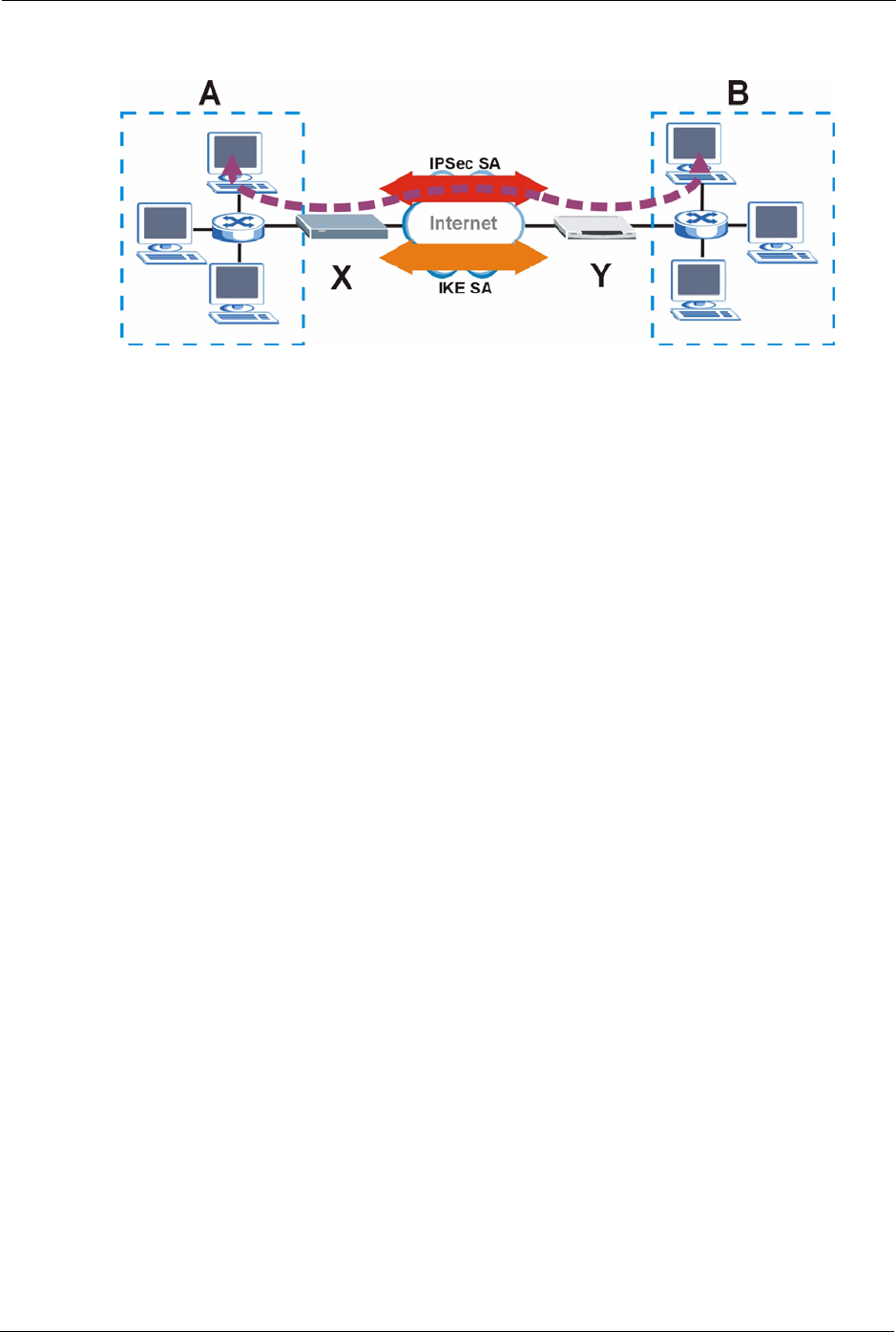
Figure 83 VPN: IKE SA and IPSec SA
In this example, a computer in network A is exchanging data with a computer in network B.
Inside networks A and B, the data is transmitted the same way data is normally transmitted in
the networks. Between routers X and Y, the data is protected by tunneling, encryption,
authentication, and other security features of the IPSec SA. The IPSec SA is established
securely using the IKE SA that routers X and Y established first.
The rest of this section discusses IKE SA and IPSec SA in more detail.
13.1.1 IKE SA (IKE Phase 1) Overview
The IKE SA provides a secure connection between the ZyXEL Device and remote IPSec
router.
It takes several steps to establish an IKE SA. The negotiation mode determines the number of
steps to use. There are two negotiation modes--main mode and aggressive mode. Main mode
provides better security, while aggressive mode is faster.
Note: Both routers must use the same negotiation mode.
These modes are discussed in more detail in Negotiation Mode on page 143. Main mode is
used in various examples in the rest of this section.
13.1.1.1 IP Addresses of the ZyXEL Device and Remote IPSec Router
In the ZyXEL Device, you have to specify the IP addresses of the ZyXEL Device and the
remote IPSec router to establish an IKE SA.
You can usually provide a static IP address or a domain name for the ZyXEL Device.
Sometimes, your ZyXEL Device might also offer another alternative, such as using the IP
address of a port or interface.
You can usually provide a static IP address or a domain name for the remote IPSec router as
well. Sometimes, you might not know the IP address of the remote IPSec router (for example,
telecommuters). In this case, you can still set up the IKE SA, but only the remote IPSec router
can initiate an IKE SA.
13.1.2 IKE SA Setup
This section provides more details about IKE SAs.


















