Managing Hypertext Transfer Protocol (HTTP) access•
Access Lists
An access list is a list of conditions that control access to the switch, router, or route processor. IP, AppleTalk,
and Internetwork Packet Exchange (IPX) access lists are like gatekeepers that control access from or to
different segments of the network. After you build an access list, it can be applied to an inbound interface or
an outbound interface. Once it has been applied to the interface, an implied “deny all” appears at the end of
each access list.
The packets are filtered by comparing an identified value and acting upon a permit or deny statement. The
list compares the packets receiving information (such as the source and destination addresses) to the values in
your access list. If a match is made, the list follows the order to permit or deny the data. If a packet is denied,
an Internet Control Message Protocol (ICMP) message is sent to the sending interface listed in the packet
header, notifying the requester that the packet has been denied.
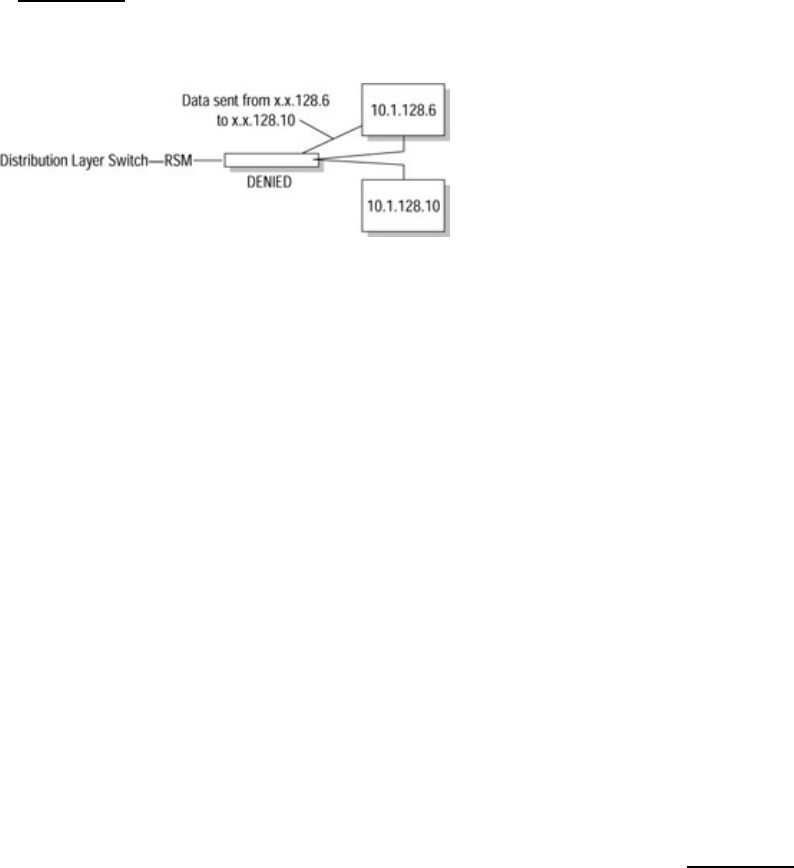
In Figure 13.2, the source address of 10.1.128.6 is trying to send a data packet to 10.1.128.10. Because the
configured access list doesn’t contain a permit statement for the source address, the access list automatically
denies the packet.
Figure 13.2: The request from x.x.128.6 to x.x.128.10 encounters an access list with no permit statement
applied to the interface. As a result, the request is denied.
Before you apply the access list to the currently used management station using a console port or virtual
terminal port, always remember to check that you have a permit statement near the top of your access list for
the management station you are using. You won’t believe how many times we have had to deal with an
administrator who is unfamiliar with access lists and who has locked himself out of his own internal or
external route processor.
Tip It is important to remember that an access list is read in the order that it is configured. Here’s an analogy:
Suppose you’re walking down a lane in a parking lot, looking for your car. Once you find your car, you
don’t continue looking. Access lists work the same way—if the access list makes a match, it does not
continue looking for further instructions.
Access List Types
There are two types of access lists: standard and extended. Both types permit or deny based on certain criteria.
The standard access list allows a permit or deny statement based only on the source address. The extended
access list is a bit more complex—it allows you to permit or deny based on the source address, destination
address, protocol type, application type, or port number of the packet.
Standard IP and IPX addresses are the easiest to configure. The configuration statement requires an access list
number, a permit or deny statement, and then the source address. This statement allows packets originating
from the identified source address to be permitted or denied through the interface to which the access list is
applied. Let’s take a look at an example of permitting the source address from Figure 13.2 on access list 2:
CAT5KRSM (config)# access−list 2 permit 10.1.128.6
To identify a subnet in one statement, use a wildcard value after the IP address. If a wildcard value is not
present, the source address must match completely. The wildcard value looks a lot like a subnet mask. A 0 in
the wildcard string indicates that the value must match exactly in the same octet as the IP address; the value
255 allows any number in the corresponding octet of the IP address to be used. Let’s look at the following
256


















