Working with the M111
Cloning the address of a wired device
3-32
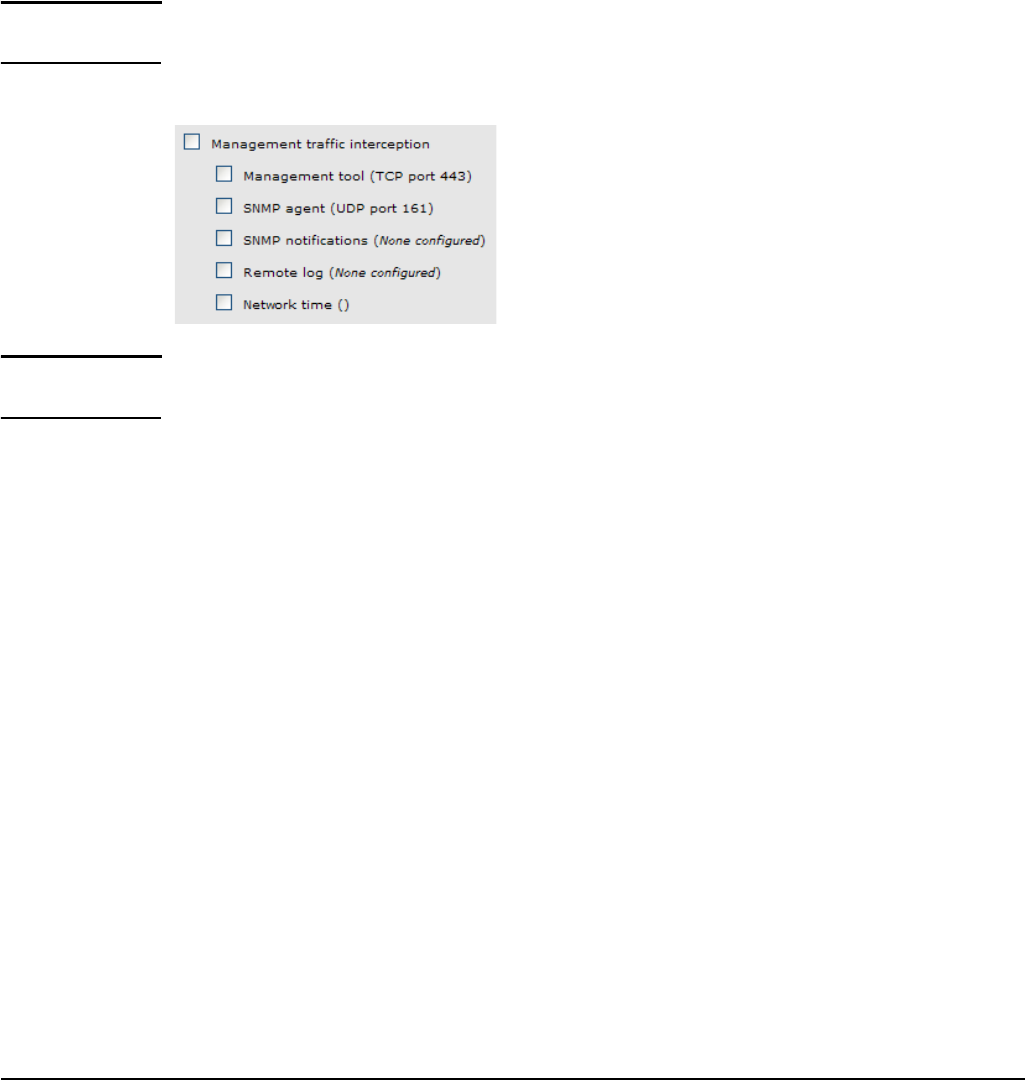
Setting up management traffic interception
The management traffic interception feature (on the Wireless > Bridging page) lets you
establish administrator logins to the M111 management tool when MAC cloning is active and
lets you intercept incoming wireless traffic on specific ports and redirect it to the M111
internal processes (M111 management tool, M111 SNMP agent, or the M111 Network Time
client) instead of forwarding it to the cloned device.
Each option displays the port that will be redirected in parenthesis. (Default values are
shown in the image below.) In most cases, the port number can be changed. Consult the
following descriptions for full details.
Note SNMP notifications and Remote log are not redirected to the management tool, as they are
both outbound.
The following options are available.
Note When using these options to reach services on the M111, you must use the IP address
assigned to the cloned device and not the original IP address assigned to the M111.
Management tool (TCP port 443)
This option enables support for administrator logins to the M111 management tool by
redirecting HTTPS traffic. If the cloned device needs to support HTTPS as well, you can
relocate the management tool port as follows:
1. Select Management > Management tool.
2. Under Web server, set Secure Web server port to 8443 (which is the common
alternative HTTPS port).
3. Under Security > Active interfaces make sure that the Wireless port is selected.
4. Select Save.
If the cloned device was at IP address 192.168.5.23, to reach the management tool you would
now specify the following in your browser: 192.168.5.23:8443.
SNMP agent (UDP port 161)
This option enables support for the SNMP agent by redirecting traffic on UDP port 161. If the
cloned device needs support to support SNMP as well, you can relocate the SNMP port as
follows:
1. Select Management > SNMP.
2. Under Attributes, set Port to a new value.