User Manual - Configuration Guide (Volume 3)
Versatile Routing Platform
Chapter 5
Configuration of IKE
5-5
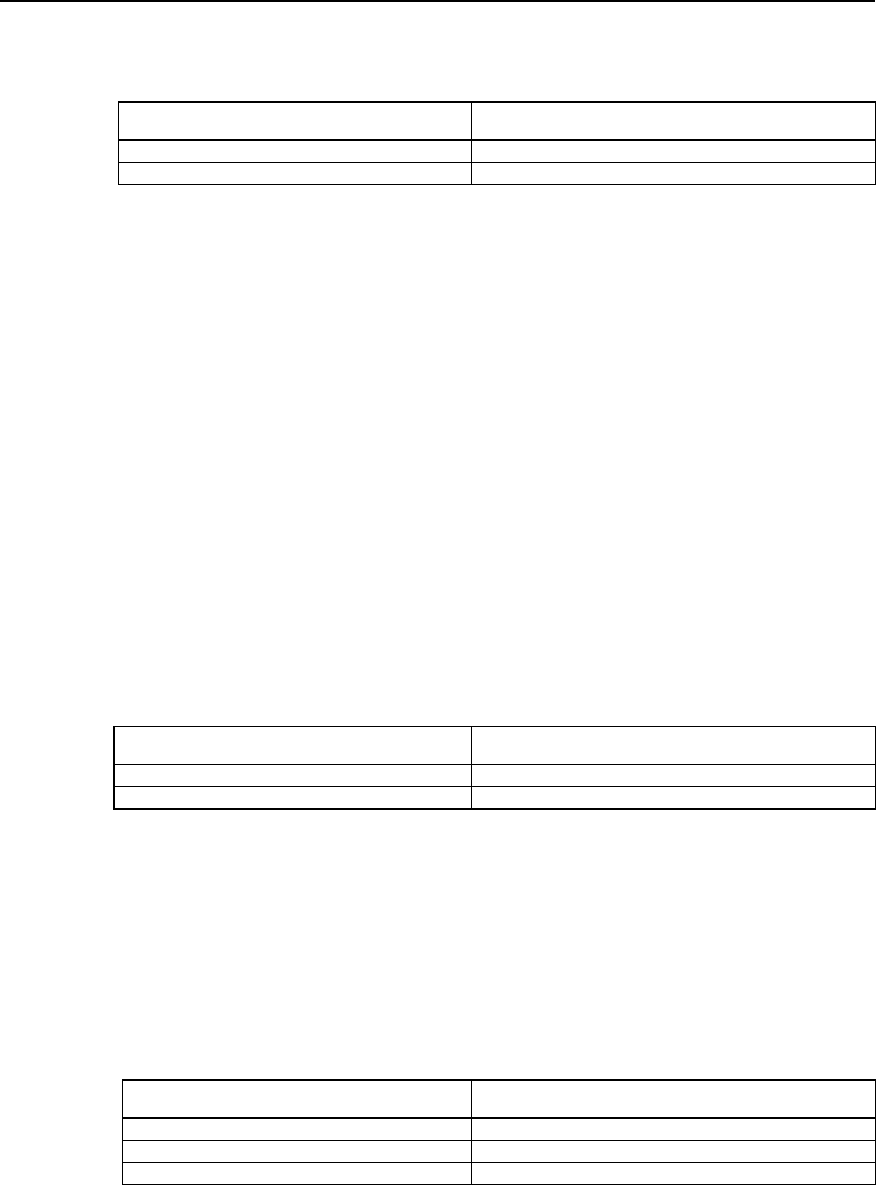
Table SC-5-6 Select DH group ID
Operation Command
Select DH group ID group {1 | 2}
Restore the default value of DH group ID no group
By default, 768-bit Diffie-Hellman group (Group 1) is selected.
5.2.8 Set Lifetime of IKE Association SA
Lifetime means how long IKE exists before it becomes invalid. When IKE begins
negotiation, the first thing for it to do is to make its security parameters of the two
parties be consistent. SA quotes the consistent parameters at each terminal, and each
terminal keeps SA until its lifetime expires. Before SA becomes invalid, it can be
negotiated by the subsequent IKE to be reused. The new SA is negotiated before the
current SA becomes invalid.
The shorter the lifetime is (to a critical point), the more secure the IKE negotiation is.
But to save time for setting IPSec, the longer IKE SA lifetime should be configured.
If the policy lifetimes of two terminals are different, only when the lifetime of originating
terminal must be greater than or equal to that of the peer end can IKE policy can be
selected, and the shorter lifetime should be selected as IKE SA lifetime.
Perform the following tasks in IKE policy configuration mode.
Table SC-5-7 Set lifetime of IKE negotiation SA
Operation Command
Set lifetime of IKE SA lifetime seconds
Set lifetime as the default value no lifetime
By default, SA lifetime is 86400 seconds (a day). It is recommended that the configured
seconds should be greater than 10 minutes.
5.3 Monitoring and Maintenance of IKE
Please perform the monitoring and maintenance in privileged user mode.
Table SC-5-8 Monitoring and maintenance of IKE
Operation Command
Show IKE security association parameter show crypto ike sa
Show IKE security policy show crypto ike policy
Clear an SA clear crypto ike sa connection-id
1) Show IKE SA parameter
Quidway# show crypto ike sa
conn-id peer flags phase doi
1 202.38.0.2 RD|ST 1 IPSEC
2 202.38.0.2 RD|ST 2 IPSEC


















