For a detailed description of prefixing as well as implementation details, see z/Architecture Principles of
Operation at http://publibz.boulder.ibm.com/epubs/pdf/dz9zr002.pdf.
5.5.2.4.8 Memory protection mechanisms
In addition to separating the address space of user and supervisor states, the z/Architecture provides
mechanisms to protect memory from unauthorized access. Memory protections are implemented using a
combination of the PSW register, a set of sixteen control registers (CRs), and a set of sixteen access registers
(ARs). The remainder of this section describes memory protection mechanisms and how they are
implemented using the PSW, CRs, and ARs.
z/Architecture provides three mechanisms for protecting the contents of main memory from destruction or
misuse by programs that contain errors or are unauthorized, low-address protection, page table protection, and
key-controlled protection. The protection mechanisms are applied independently at different stages of
address translation. Access to main memory is only permitted when none of the mechanisms prohibit access.
Low-address protection is applied to effective addresses, page table protection is applied to virtual addresses
while they are being translated into real addresses, and key-controlled protection is applied to absolute
addresses.
5.5.2.4.8.1 Low-address protection
The low-address protection mechanism provides protection against the destruction of main memory
information used by the CPU during interrupt processing. This is implemented by preventing instructions
from writing to addresses in the ranges 0 through 511 and 4096 through 4607 (the first 512 bytes of each of
the first and second 4 KB address blocks).
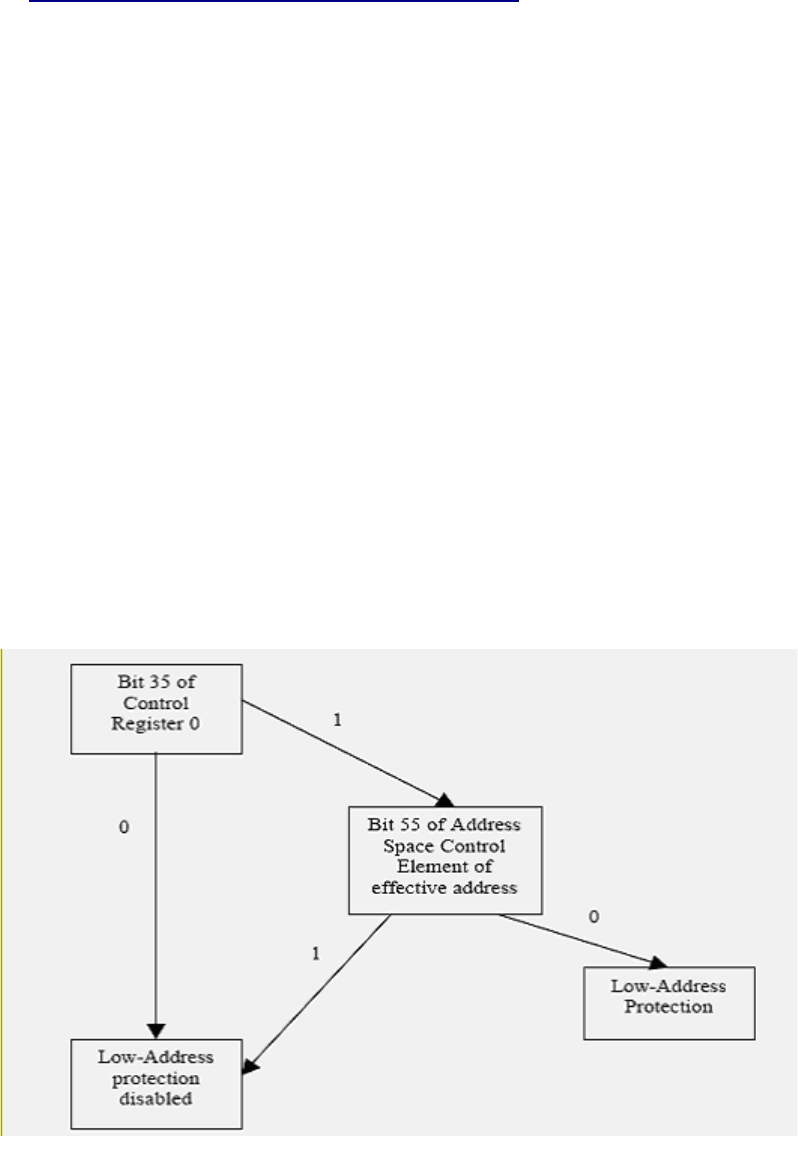
Low-address protection is applied to effective addresses only if the following bit positions are set in control
register 0 and the ASCE of the address space to which the effective address belongs.
111
Figure 5-53: Low-address protection on effective address


















