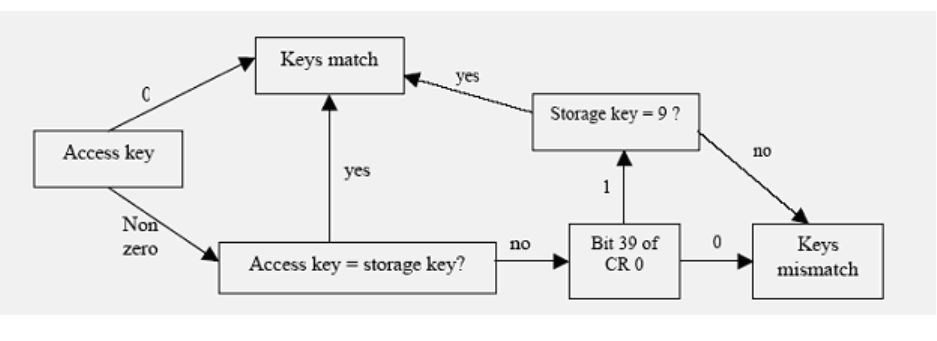
5.5.2.4.8.3 Key-controlled protection
When an access attempt is made to an absolute address, which refers to a memory location, key-controlled
protection is applied. Each 4K page, real memory location, has a 7-bit storage key associated with it. These
storage keys for pages can only be set when the processor is in the supervisor state. The Program Status
Word contains an access key corresponding to the current running program. Key-controlled protection is
based on using the access key and the storage key to evaluate whether access to a specific memory location is
granted.
The 7-bit storage key consists of access control bits (0, 1, 2, and 3), fetch protection bit (4), reference bit (5),
and change bit (6). The following two diagrams show the key-controlled protection process.
The z/Architecture allows for fetch protection override for key-controlled protection. The following diagram
describes how fetch protection override can be used. Currently, SLES does not set the fetch protection bit of
the storage key.
115
Figure 5-56: Key match logic for key-controlled protection


















