5.12.1.1 Concepts
SSL is used to authenticate endpoints and to secure the contents of the application-level communication. An
SSL-secured connection begins by establishing the identities of the peers, and establishing an encryption
method and key in a secure way. Application-level communication can then begin. All incoming traffic is
decrypted by the intermediate SSL layer and then forwarded on to the application; outgoing traffic is
encrypted by the SSL layer before transmission.
SSL uses encryption with symmetric keys for data transfer, encryption with asymmetric keys for exchanging
symmetric keys, and one-way hash functions for data integrity. The following sections briefly describe
encryption and message-digest concepts, and how they are used to implement data confidentiality, data
integrity, and the authentication mechanism.
5.12.1.1.1 Encryption
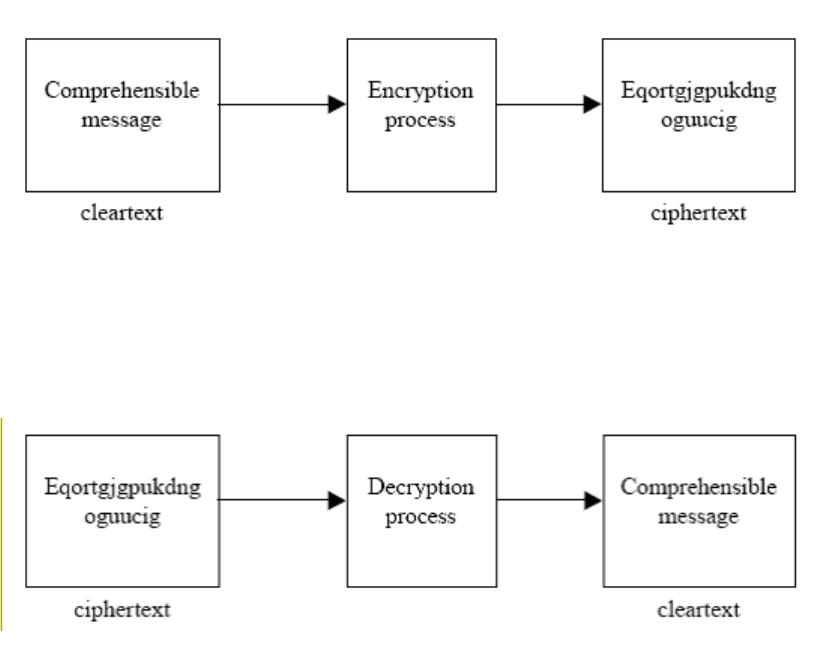
Encryption is a process of disguising a message. Encryption transforms a clear-text message into cipher text.
Decryption converts cipher text back into the original, comprehensible clear text.
Most encryption processes involve the use of an algorithm and a key. For example, in the previous
illustration, the algorithm was “replace alphabets by moving forward” and the key was 2.
182
Figure 5-86: Decryption
Figure 5-85: Encryption


















