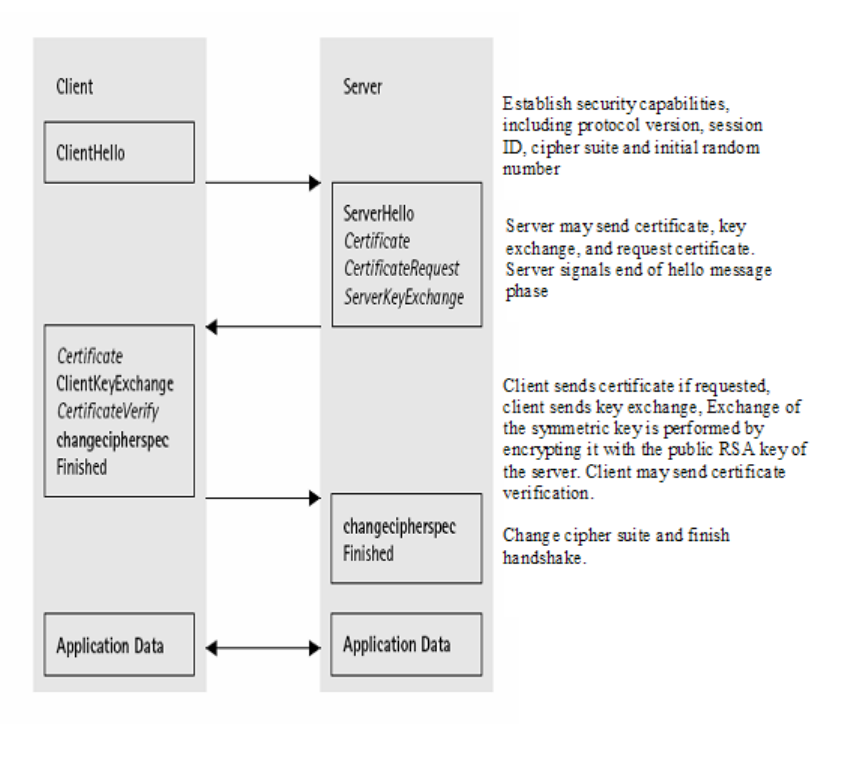
1. Client hello message: The CipherSuite list, passed from the client to the server in the client hello
message, contains the combinations of cryptographic algorithms supported by the client in order of
the client's preference (first choice first). Each CipherSuite defines both a key exchange algorithm
and a CipherSpec. The server selects a cipher suite or, if no acceptable choices are presented, returns
a handshake failure alert and closes the connection.
2. Server key exchange message: The server key exchange message is sent by the server if it has no
certificate, has a certificate only used for signing (that is, DSS [DSS] certificates, or signing-only
RSA [RSA] certificates), or FORTEZZA KEA key exchange. This message is not used if the server
certificate contains Diffie-Hellman [DH1] parameters.
3. Client key exchange message (RSA encrypted premaster secret message): In the evaluated
configuration, RSA is used for key agreement and authentication. The client generates a 48-byte pre-
master secret, encrypts it under the public key from the server's certificate or temporary RSA key
from a server key exchange message, and sends the result in an encrypted premaster secret message.
4. Certificate verify message: This message is used to provide explicit verification of a client certificate.
This message is only sent following any client certificate that has signing capability (that is, all
certificates except those containing fixed Diffie-Hellman parameters).
187
Figure 5-91: Handshake protocol (optional or content-dependent handshake messages
are in italic type)


















