4.1.2.3 Programs with software privilege
Examples of programs running with software privilege are:
• Programs that are run by the system, such as the cron and init daemons.
• Programs that are run by trusted administrators to perform system administration.
• Programs that run with privileged identity by executing setuid programs.
All software that runs with hardware privileges or software privileges, and that implements security enforcing
functions, is part of the TOE Security Functions (TSF). All other programs are either unprivileged programs
that run with the identity of the user that invoked the program, or software that executes with privileges but
does not implement any security functions.
In a properly administered system, unprivileged software is subject to the security policies of the system and
does not have any means of bypassing the enforcement mechanisms. This unprivileged software need not be
trusted in any way, and is thus referred to as untrusted software. Trusted processes that do not implement any
security function need to be protected from unauthorized tampering using the security functions of the SLES.
They need to be trusted to not perform any function that violates the security policy of the SLES.
4.2 TOE Security Functions software structure
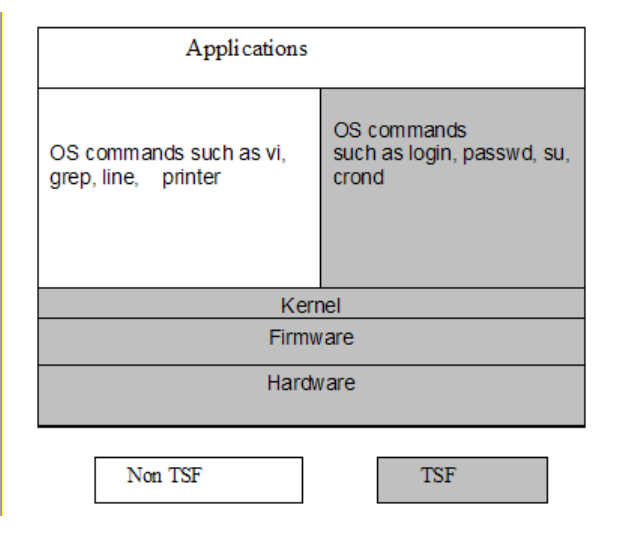
This section describes the structure of the SLES software that constitutes the TOE Security Functions (TSF).
The SLES system is a multi-user operating system, with the kernel running in a privileged hardware mode,
and the user processes running in user mode. The TSF includes both the kernel software and certain trusted
non-kernel processes.
Figure 4-2 depicts the TSF and non-TSF portions of software. Subsequent sections provide more detailed
descriptions of the kernel and non-kernel TSF architectural subsystems.
22
Figure 4-2: TSF and non-TSF software


















