The phrase data integrity implies that the data received is as it was when sent. It has not been tampered,
altered, or impaired in any way. Data authentication ensures that the sender of the data is really who you
believe it to be. Without data authentication and integrity, someone can intercept a datagram and alter the
contents to reflect something other than what was sent, as well as who sent it. IP Security provides data
authentication and integrity through the use of hash functions in message authentication codes (HMACs).
The encryption algorithms and HMACs require several shared symmetric encryption keys. Thus IP Security
also takes into consideration key management, and the secure exchange of keys through its services.
This introduction briefly describes the collection of protocols and services offered in IP Security.
5.4.3.4.1 Functional Description of IPsec
IP Security provides security at the IP Layer through the use of the AH and ESP protocols. These protocols
operate in transport and tunnel mode.
In transport mode, AH and ESP provide security to the upper-layer protocols of the TCPIP protocol stack
(that is, UDP and TCPIP). Therefore, only part of the IP datagram is protected. Transport mode is usually
used for security between two hosts.
In tunnel mode, AH and ESP provide security to the entire IP datagram. The entire original IP datagram is
encapsulated, and an outer IP header attached. Tunnel mode is usually for security between two gateways
(that is, networks) or between a host and a gateway.
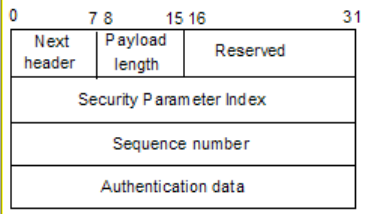
5.4.3.4.1.1 AH Protocol (AH)
The IP Authentication (AH) Header is described in RFC 2402. Besides providing data integrity and
authentication of source, it also protects against replay attacks via the use of a sequence number and replay
window.
The contents of the IP datagram, along with the shared secret key, are hashed, resulting in a digest. This digest
is placed in the AH header, and the AH header is then included in the packet.
Verification occurs when the receiving end removes the AH header, then hashes its shared secret key with the
IP datagram to produce a temporary digest and compare it with the digest in the AH header. If the two digests
are identical, verification has succeeded.
AH Header
When used in transport mode, the AH header is placed before the upper-layer protocol, which it will protect,
and after the IP header and any options for IPv4. In the context of IPv6, according to RFC 2402, AH is
viewed as an end-to-end payload. Therefore, the AH header should appear after the IP headers and hop-by-
hop, routing, and fragmentation extension headers if present.
An IP Packet with transport mode AH
75


















