5.11 Identification and authentication
Identification is when a user possesses an identity to a system in the form of a login ID. Identification
establishes user accountability and access restrictions for actions on the system. Authentication is verification
that the user’s claimed identity is valid, and is implemented through a user password at login time.
All discretionary access-control decisions made by the kernel are based on the process’s user ID established at
login time and all mandatory access control decisions made by the kernel are based on the process domain
established through login, which make the authentication process a critical component of a system.
The TOE implements identification and authentication through a set of trusted programs and protected
databases. These trusted programs use an authentication infrastructure called the Pluggable Authentication
Module (PAM). PAM allows different trusted programs to follow a consistent authentication policy. PAM
171
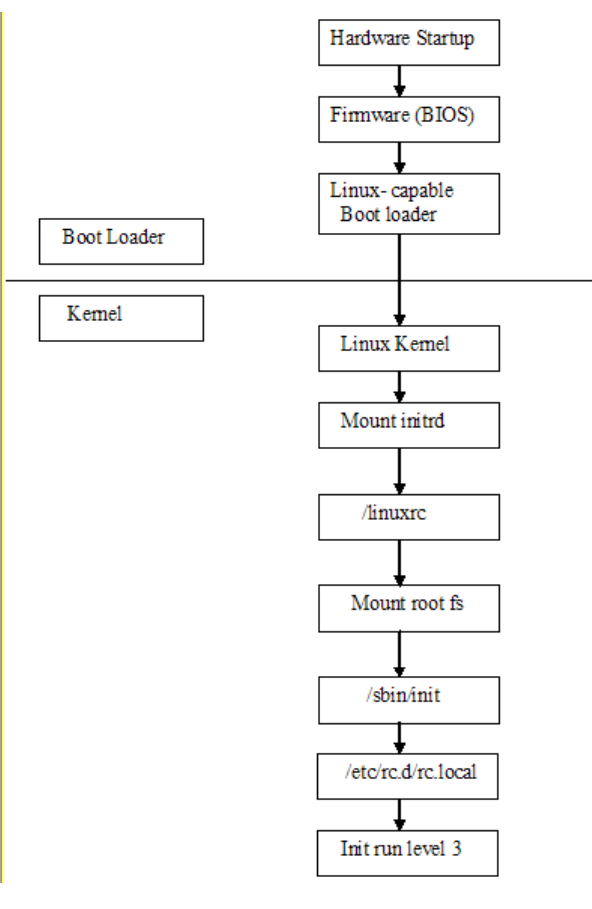
Figure 5-83: eServer 326 SLES boot sequence


















