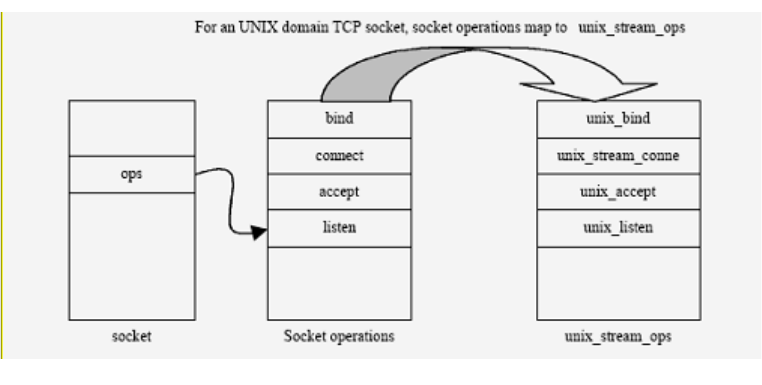
Similarly, for UNIX domain sockets, bind() invokes unix_bind(). unix_bind() creates an entry in
the regular ext3 file system space. This process of creating an entry for a socket in the regular file system
space has to undergo all file system access control restrictions. The socket exists in the regular ext3 file
system space, and honors DAC policies of the ext3 file system. bind() may perform additional access
control checks by calling the security_socket_bind() LSM hook, but the SLES kernel does not use
this LSM hook. bind() does not create any data objects that are accessible to users, so there are no object
reuse issues to handle.
5.4.5.3 listen()
listen() indicates a willingness to accept incoming connections on a particular socket. A queue limit for
the number of incoming connections is specified with listen(). Other than checking the queue limit,
listen() does not perform DAC. It may perform additional access control checks by calling the
security_socket_listen() LSM hook but the SLES kernel does not use this hook. listen()
does not create any data objects that are accessible to users, so there are no object reuse issues to handle.
Only TCP sockets support the listen() system call.
5.4.5.4 accept()
accept() accepts a connection on a socket. accept() does not perform any access control. accept()
does not create any data objects that are accessible to users and therefore there are no object reuse issues to
handle. Only TCP sockets support accept() system call.
5.4.5.5 connect()
connect() initiates a connection on a socket. The socket must be listening for connections; otherwise, the
system call returns an error. Depending upon the type of the socket (stream for TCP or datagram for UDP),
connect() invokes the appropriate domain type specific connection function. connect() does not
perform DAC. It may perform additional access control checks by calling the
security_socket_connect() LSM hook, but the SLES kernel does not use this hook. connect()
does not create any data objects that are accessible to users, so there are no object reuse issues to handle.
81
Figure 5-21: bind() function for UNIX domain TCP socket


















