YML9WMAXXN ADSL2+ Wireless N300 Modem Router with VoIP User Guide
www.netcomm.com.au 33
NetComm Gateway
TM
Series - ADSL2+ Wireless N300 Modem Router with VoIP
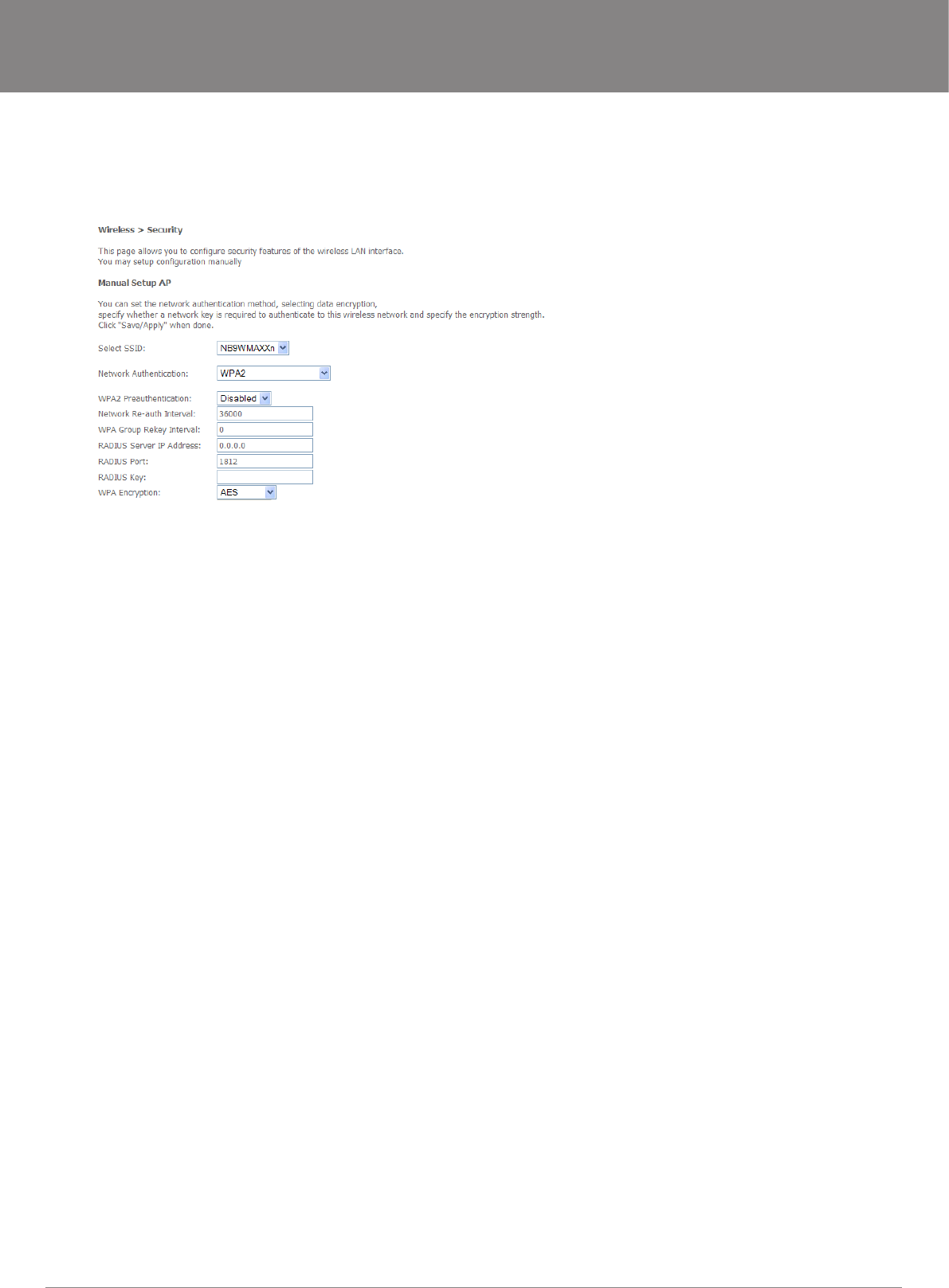
Quick Security Setup 2 – WPA-PSK
If a stronger network security settings is required, go to Wireless>Security and select WPA-PSK from the Network Authentication drop-
down menu. Enter a network key of your choice in the WPA Pre-Shared Key eld; this can be from 8 to 63 characters and contain special
characters and spaced. And change the WPA Group Rekey Interval to 3600.
Select TKIP for WPA Encryption and leave WEP Encryption as disabled.
Users wishing to connect to your network will need to know the SSID name and the WPA Pre-Shared Key.
Note: Wireless client network cards must be WPA-compliant to connect to your network; if in doubt check the wireless client network card documentation, or use WEP security
(above).
6.3 Wireless Security in Detail
The following provides a detailed summary of wireless terms and acronyms and more in-depth explanations of the topic. It assumes
little prior knowledge of wireless networking and is aimed at providing background for the terminology used in the NB9WMAXXn Wireless
Security screens.
Warning: Wireless Networking is a technically challenging subject!
Authentication and Encryption
The two major aims of wireless network security are:
(1) to prevent unauthorised persons from joining the network and
(2) to prevent interception of network data or ‘eavesdropping’. These aims are accomplished by:
• Authentication: establishes the identity of those seeking to join the network
• Encryption: ensures that data is protected in such a way that those outside the network cannot access it.
Network Keys
The term ‘network key’ is often used in the context of wireless networking. The Network Key can be a text string, although in some
systems network keys are generated from a ‘pass-phrase’ which is entered in one eld from which up to four keys are derived in elds
underneath the entry eld.
In all cases, the Wireless Router/Access Point and the workstations wishing to connect must use the same Network Key which needs to be
communicated to clients prior to connection.
‘Re-keying’ refers to the frequency with which network keys are changed; for security purposes, they need to be changed frequently in
case they re-occur frequently enough to identify them.
In some wireless systems, network keys are entered by a variety of means including:
• ASCII – any letter, number, or punctuation mark but no special characters
• Hex – Letters A-F, Numbers 0-9 only
• Pass phrase – enter a phrase in the top eld of a set of elds, an algorithm then generates a series of keys based on the entered values.
These methods have been standardised in the later implementations of Wireless Security and are easier to use in WPA.


















