ADSL2+ Wireless N300 Modem Router with VoIP User Guide YML9WMAXXN
34 www.netcomm.com.au
WEP and WPA
“WEP” stands for Wired Equivalent Privacy and was the original wireless security method. Over time it was found to be vulnerable to
attacks based on de-coding the ‘keys’ used to encrypt the data. While no longer recommended for enterprise-level security, WEP
is certainly secure from casual interception and will repel any non-specialised attempt to join the network or intercept data; it can be
penetrated with various kinds of software tools and techniques but these are beyond the capability of the average computer user.
‘WPA’ stands for Wi-Fi Protected Access and is an improvement on WEP. WPA2 offers further renements to WPA.
WPA and WPA2 both comprise a number of different wireless security elements and methods that can be adapted to a variety of situations
depending on the requirements. A lot of what is provided is applicable to enterprise-level wireless networking, in other words, suitable for
businesses who wish to deploy strict security methods and policies for their employees. Accordingly, these technologies will exceed the
requirements of home users.
An important element of WPA security is a RADIUS server (stands for Remote Access Dial-in User Service). The RADIUS server typically sits in
the server room of a business or department and authenticates and manages user requests for connection. Home users will generally never
have to bother about RADIUS server details.
In nearly all cases, the default security method, which is WEP, or WPA-PSK will provide adequate security for home wireless networks.
Other wireless security elements shall be explained in context below.
Network Authentication
Network Authentication species the type of network authentication. The default value is ‘Shared’.
Open: Under Open System authentication, any wireless station can request authentication.
Shared: Under Shared Key authentication, each wireless station is assumed to have received a secret shared key over a
secure channel that is independent from the 802.11 wireless network communications channel (i.e. verbally). To
use Shared Key authentication, you must have a network key assigned to the clients trying to connect to your
NB9WMAXXn.
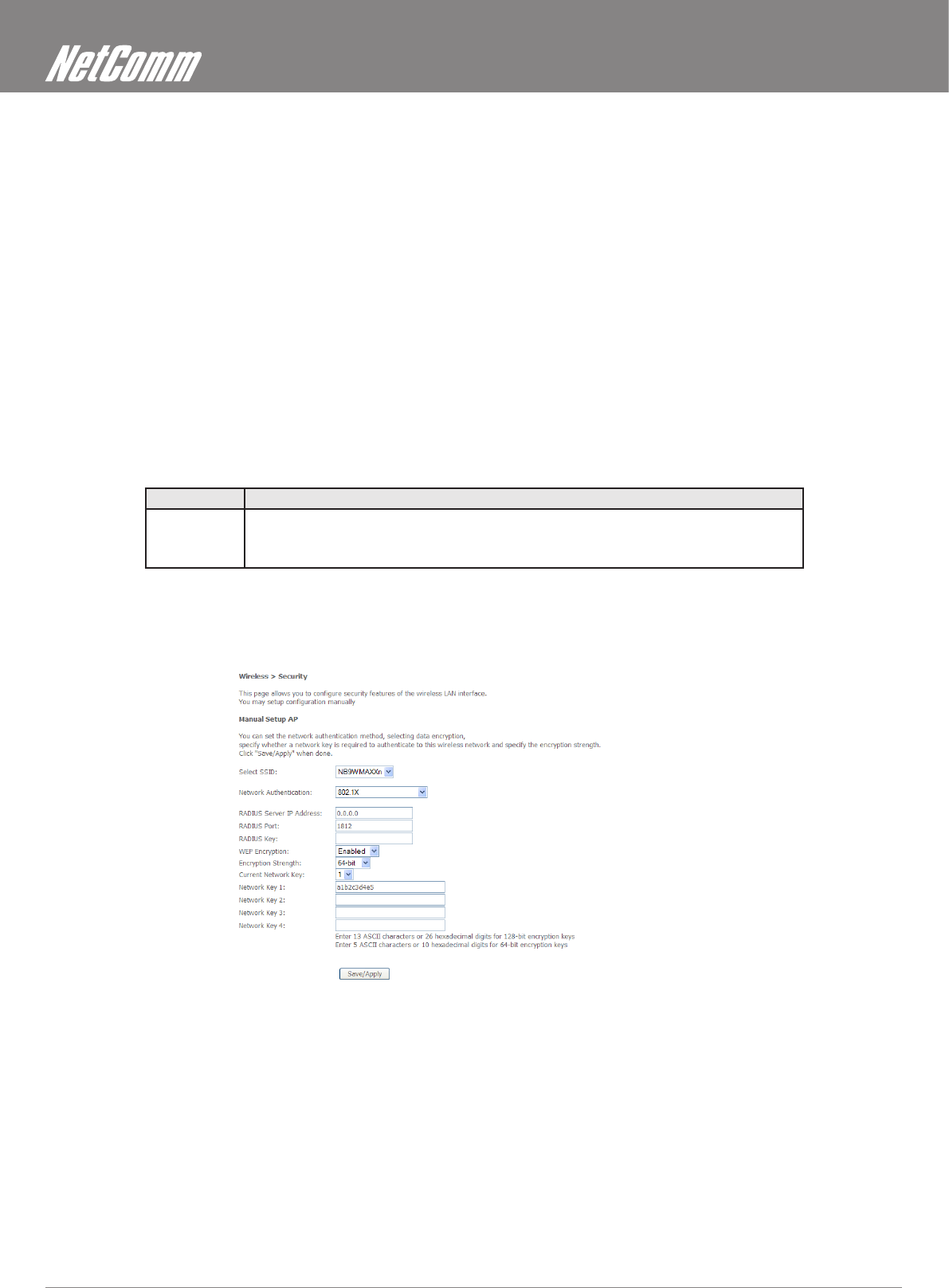
802.1X
802.1X security requires the presence of a RADIUS server, and specication of the IP address of a RADIUS server, the port on which to
connect to it, and the Shared Key used to authenticate with it.
Disregard this security setting unless you are setting up or connecting to a RADIUS server.
WPA
WPA requires a RADIUS server to provide client authentication. WPA also requires specication of the ‘WPA Group Rekey Interval’ which
is the rate that the RADIUS server sends a new Group Key out to all clients. The Re-Keying process is part of WPA’s enhanced security.
This method also requires specication of the IP address of a RADIUS server, the port on which to connect to the RADIUS server, and the
shared key used to authenticate with the RADIUS server.


















