Reference Manual for the 54 Mbps Wireless ADSL Firewall Router DG834G
Wireless Networking Basics D-5
202-10006-01
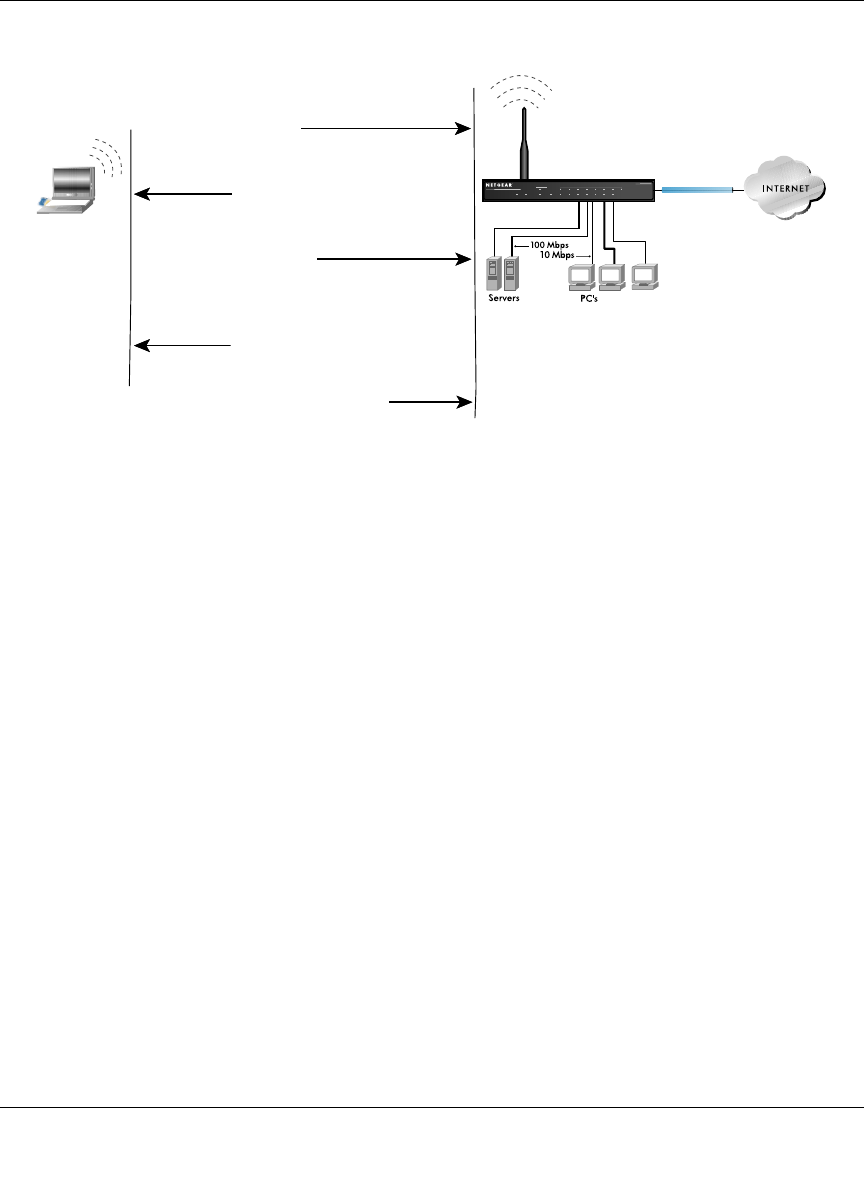
Figure D-2: 802.11b shared key authentication
Overview of WEP Parameters
Before enabling WEP on an 802.11b network, you must first consider what type of encryption you
require and the key size you want to use. Typically, there are three WEP Encryption options
available for 802.11b products:
1. Do Not Use WEP: The 802.11b network does not encrypt data. For authentication purposes, the
network uses Open System Authentication.
2. Use WEP for Encryption: A transmitting 802.11b device encrypts the data portion of every
packet it sends using a configured WEP Key. The receiving 802.11b device decrypts the data using
the same WEP Key. For authentication purposes, the 802.11b network uses Open System
Authentication.
3. Use WEP for Authentication and Encryption: A transmitting 802.11b device encrypts the
data portion of every packet it sends using a configured WEP Key. The receiving 802.11b device
decrypts the data using the same WEP Key. For authentication purposes, the 802.11b network uses
Shared Key Authentication.
Note: Some 802.11b access points also support Use WEP for Authentication Only (Shared Key
Authentication without data encryption).
INTERNET LOCAL
ACT
12345678
LNK
LNK/ACT
100
Cable/DSL
ProSafeWirelessVPN Security Firewall
MODEL
FVM318
PWR TEST
WLAN
Enable
Access Point1) Authentication
request sent to AP
2) AP sends challenge text
3) Client encrypts
challenge text and
sends it back to AP
4) AP decrypts,and if correct,
authenticates client
5) Client connects to network
802.11b Authentication
Shared Key Steps
Client
attempting
to connect
Router


















