7-19
Using Passwords, Port Security, and Authorized IP Managers To Protect Against Unauthorized Access
Configuring and Monitoring Port Security
Using Passwords, Port
Security, and Authorized IP
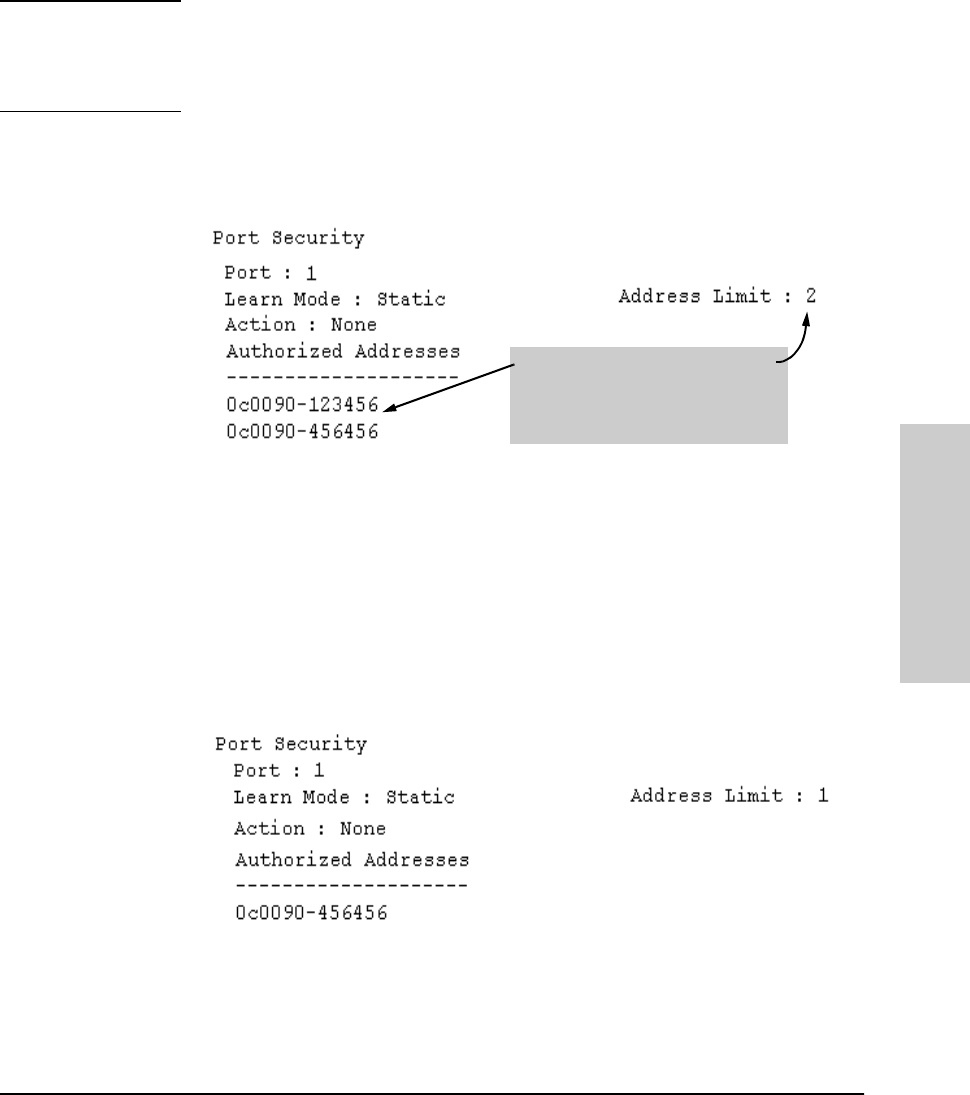
Note You can reduce the address limit below the number of currently authorized
addresses on a port. This enables you to subsequently remove a device from
the “Authorized” list without opening the possibility for an unwanted device
to automatically become authorized.
For example, suppose port 1 is configured as shown below and you want to
remove 0c0090-123456 from the Authorized Address list:
The following command serves this purpose by removing 0c0090-123456 and
reducing the Address Limit to 1:
SMC TigerSwitch 10/100(config) # port-security 1 address-
limit 1
SMC TigerSwitch 10/100(config) # no port-security 1 mac-
address 0c0090-123456
The above command sequence results in the following configuration for port 1:
When removing 0c0090-123456, first
reduce the Address Limit by 1 to prevent
the port from automatically adding
another device that it detects on the
network.


















