Chapter 4
Advanced Configuration
32
4-Port SSL/IPSec VPN Router
Time The time interval to which the access rule applies
is displayed.
Day The days to which the access rule applies is
displayed.
Click Edit to edit an access rule, and click the Trash Can
icon to delete an access rule. If the Access Rules table
has multiple pages, select a different page to view from
the Jump to drop-down menu. If you want more or fewer
entries listed per page, select a different number from the
entries per page drop-down menu.
Click Add New Rule to add new access rules, and the Add
a New Access Rule screen appears.
Click the Restore to Default Rules to restore the default
rules and delete the custom access rules.
Add a New Access Rule
Add a New Access Rule
Services
Policy Name Enter a name for the new access rule.
Action Select Allow or Deny, depending on the purpose
of the access rule.
Service Select the Service you want.
If the Service you need is not listed in the menu, click
Service Management to add the new service. The Service
Management screen appears.
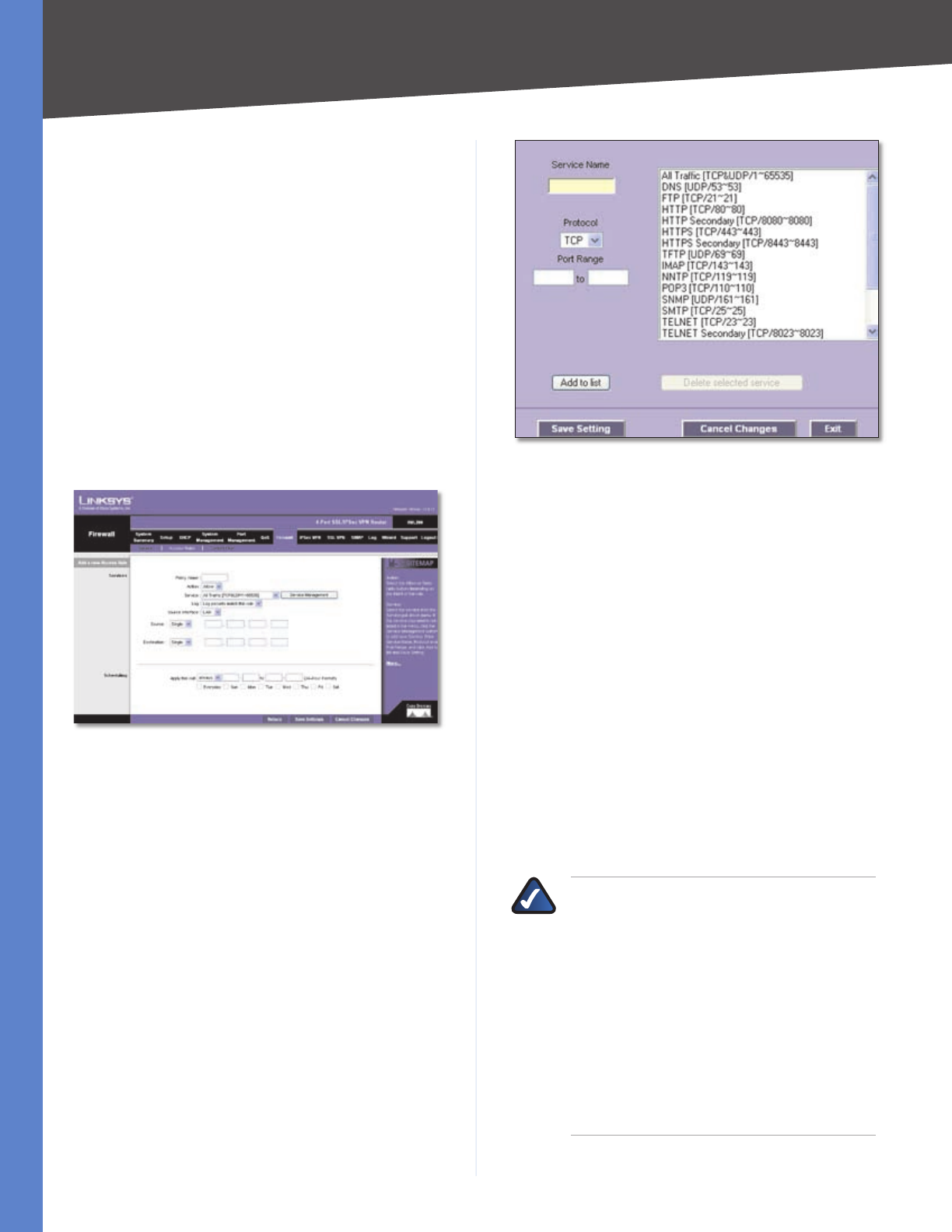
Service Management
Service Name Enter a name.
Protocol Select the protocol it uses.
Port Range Enter its range.
Click Add to List. Click Save Settings to save your changes,
or click Cancel Changes to undo them. Click Exit to return
to the Add a New Access Rule screen.
If you want to modify a service you have created, select it
and click Update this service. Make changes. Click Save
Settings to save your changes, or click Cancel Changes
to undo them. Click Exit to return to the Add a New Access
Rule screen.
If you want to delete a service you have created, select it
and click Delete selected service. Click Save Settings to
save your changes, or click Cancel Changes to undo them.
Click Exit to return to the Add a New Access Rule screen.
Log The Router can keep a log tracking this type of
activity. To keep a log, select Log packets match this
access rule. If you do not want a log, select Not log.
NOTE: If the Deny Policies option is enabled on
the Log > System Log screen, then the log will
not include log events from the Deny access
rules on the Firewall > Access Rules screen.
Log events from the Deny access rules will be
logged separately from Deny Policies if the
option, Log packets match this rule, is selected.
If the Allow Policies option is enabled on the Log
> System Log screen, then the log will include
log events from the Allow access rules on the
Firewall > Access Rules screen, regardless of the
option, Log packets match this rule.
Source Interface Select WAN, LAN, or Any.


















