xStack
®
DES-3200-10/18/28/28F Layer 2 Ethernet Managed Switch User Manual
common ARP Spoofing attack that is wide spread today. This is why the Packet Content ACL is
able to inspect any specified content of a packet in different protocol layers.
Click Apply to implement changes made.
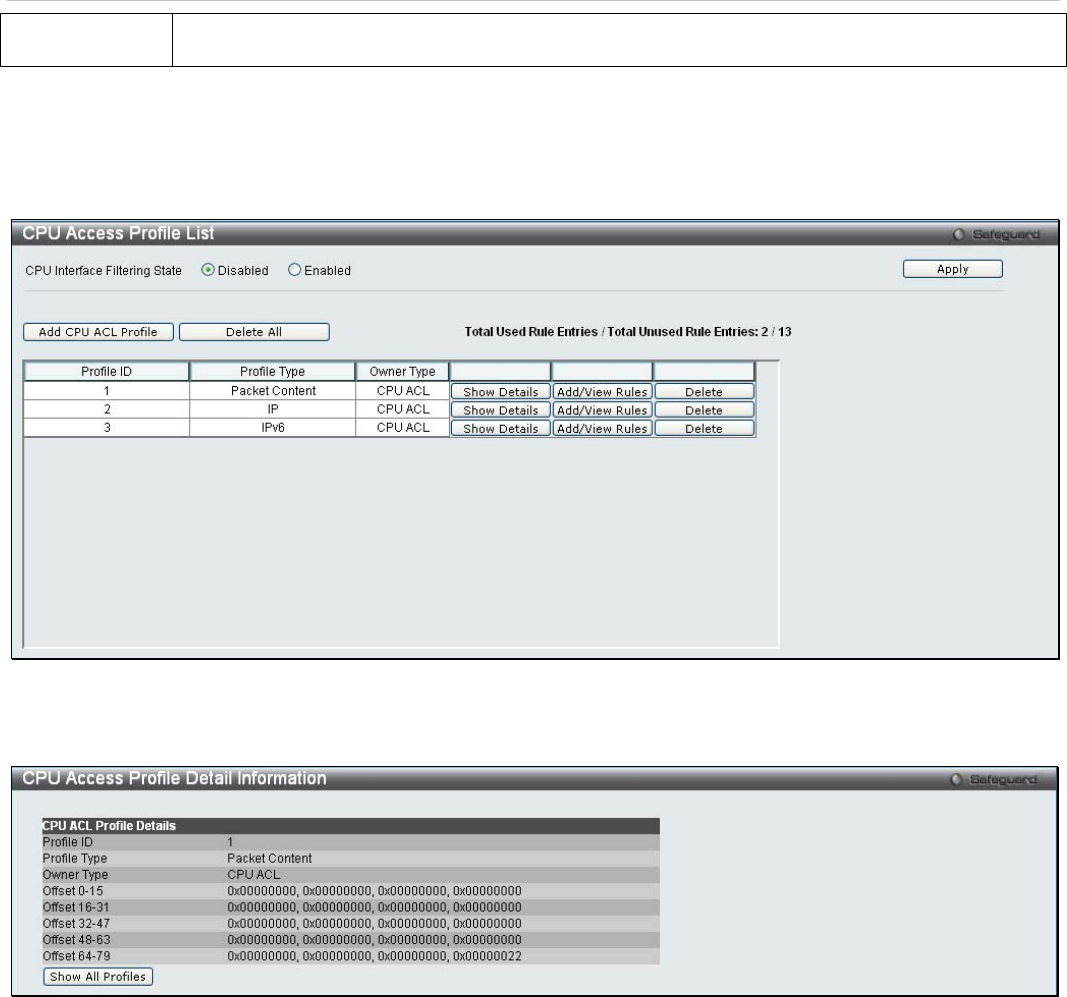
Click Create to view the new CPU Access Profile List entry in the CPU Access Profile List window shown below. To
add another CPU Access Profile, click Add CPU ACL Profile. To delete a profile, click the corresponding Delete
button. To view the specific configurations for an entry, click the Show Details button. To add a rule to the CPU
Access Profile entry, click the Add/View Rules button.
Figure 6 - 49. CPU Access Profile List window for Packet Content example
To view the configurations for a previously configured entry, click on the corresponding Show Details button, which
will display the following window:
Figure 6 - 50. CPU Access Profile Detail Information window for Packet Content example
To return to the CPU Access Profile List window, click Show All Profiles. To add a rule to a previously configured
entry, click on the corresponding Add/View Rules button and then Add Rule, which will reveal the following window:
180


















