114 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
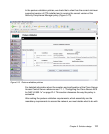
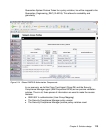
The Cisco Secure ACS evaluates each of the authorization rules in order from
top to bottom. The first match assigns the client the listed posture token. If no
match is found, the default rule assigns the listed token.
Assigning the System Posture Token
Cisco Secure ACS supports the following System Posture Token types:
Healthy The endpoint device complies with the currently required
credentials so you do not have to restrict this device.
Checkup The endpoint device is within the policy but does not have
the latest security software. We recommend an update.
Use to proactively remediate a host to the Healthy state.
Quarantine The endpoint device is out of policy and must be restricted
to a remediation network. The device is not actively
placing a threat on other hosts, but is susceptible to attack
or infection and should be updated as soon as possible.
Transition The endpoint device is in the process of having its posture
checked and is given interim access pending a result from
a full posture validation. This is applicable during host
boot where all services may not be running or while audit
results are not yet available.
Infected The endpoint device is an active threat to other hosts.
Network access should be severely restricted and placed
into remediation or totally denied all network access.
Unknown The posture credentials of the endpoint device cannot be
determined. Quarantine the host and audit, or remediate
until a definitive posture can be determined.
In our scenario we only use Healthy and Quarantine.
Healthy indicates that the
system is in full compliance and is therefore granted full network access.
Quarantined indicates that the system has a violation count of at least one and
the system is denied access to the network until remediation has taken place.
There should not be an
unknown system in the ACS. This is because we are
using IEEE 802.1x. Should the user fail IEEE 802.1x authentication, the user will
not have any network access, or may be granted access to the guest VLAN
configured on the switch, depending on your network policy, as in some
situations it may be desirable to allow unknown systems access to the Internet
(for example, visitors or contractors).
At the time of writing this book, downloadable Access Control Lists were not
supported when using NAC L2 802.1x. Therefore, the Access Control Lists are
defined on the NAD, in our case a Layer-3 capable Cisco 3750 switch. Switched
Virtual Interfaces (SVIs) were defined, and the access lists were bound to these