Chapter 2. Architecting the solution 31
reason a policy cannot be complied with due to a particular business need, the
situation has to be accepted as a security risk for a well-defined period of time
and signed off by the project sponsor.
A policy that is created but is not enforced is no better than no security policy at
all. This situation can expose the organization and put its credibility at stake.
We discuss more details of the full policy life cycle in the following sections.
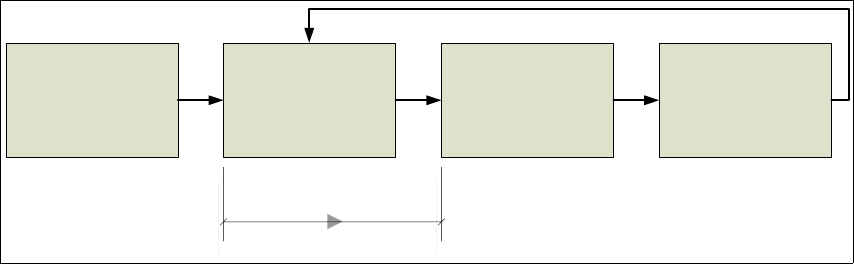
Figure 2-7 depicts the single steps in the security policy life cycle management
process.
Figure 2-7 Security policy life cycle diagram
Creation
Chapter 1, “Business context” on page 3, discussed business reasons for having
security policies in place. At this point we want to mention only that for the
automated audit most of the policies have be operationalized. For example, the
policy statement (such as “Each workstation connected to the corporate network
should have all of the latest recommended security patches applied”) must be
translated into a detailed list of all patches and hotfixes required for each
operating system type.
This process is described in detail in the IBM Redbook Deployment Guide
Series: IBM Tivoli Security Compliance Manager, SG24-6450.
Implementation
Establishing and implementing the policy in the environment typically are two
separate processes involving different business units. IBM Tivoli Security
Compliance Manager is an audit tool for automated verification of compliance. As
part of the security audit process, it is not designed to perform any changes to
the configuration of audited systems.
Security Policy Creation
Security Policy
Implementation in the
environment
Security Policy
Enforcement
Security Policy
Review and update
Grace Period


















