Chapter 6. Compliance subsystem implementation 161
11.After the wizard is closed you will see the imported policy in the Administrative
Console, as shown in Figure 6-36.
Figure 6-36 Compliance Policy view
To import the additional two sample policies named
IISSCN_TCM_v2.00_winXP.pol and IISSCN_TCM_v2.00_win2000.pol, repeat
steps 6 to 10, selecting the correct files accordingly.
6.2.4 Customization of compliance policies
To begin with the process of building customized polices for your environment
we first need to explain the role of the policies imported in the previous section.
There are a total of three policies, and two of them have names that are
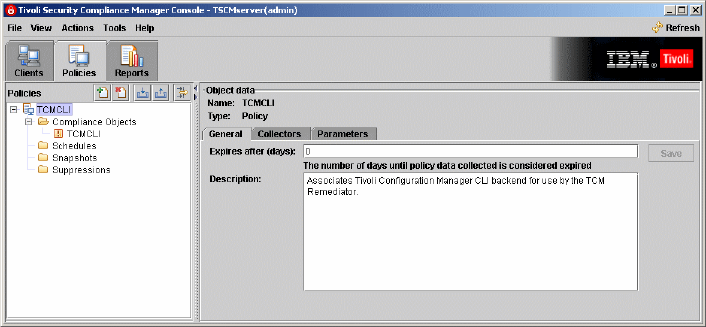
self-explanatory. The third policy, named TCMCLI, is the one that is special.
This policy must be assigned to every client that is supposed to use the auto
remediation feature. This policy is not checking anything on the client. The only
task of this policy is to distribute the correct level of Tivoli Configuration Manager
stand-alone command-line utilities to the clients, which are then used to install
the software package blocks downloaded from the Software Package Web
Server during the remediation process.
Moving forward in the next section we describe the process of customizing the
IISSCN_TCM_v2.00_winXP policy to meet the needs described in the first
paragraph of 6.2, “Configuration of the compliance policies” on page 152.
We start with customizing the Symantec Antivirus compliance check. As
opposed to the normal Tivoli Security Compliance Manager compliance checks,
which are performed on the server based on the data collected from the clients
and stored in the database, the policies used for Network Admission Control