190 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
book we cover only the installation of the client on Windows. For other platforms
and more detailed system prerequisites see Tivoli Security Compliance
Manager: Installation Guide: Client Component, GC32-1593. A prerequisite for
the Security Compliance Manager client to work within the IBM Integrated
Security Solution for Cisco Networks is the already deployed Cisco Trust Agent.
This is why we first cover the installation of this component.
6.3.1 Cisco Trust Agent
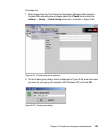
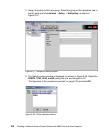
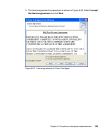
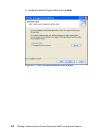
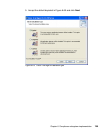
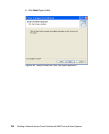
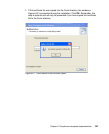
The installation of the Cisco Trust Agent is an essential part of the client software
deployment. It requires three steps to be performed, which in specific cases can
be combined into two or even into one. These three steps are:
1. Installation of the Cisco Trust Agent base code
2. Installation of the ACS server certificate
3. Installation of one or more posture plug-ins
Prerequisites
Since the release of NAC phase 2, the Cisco Trust Agent version has been
updated, and is available in two different options. There is the Cisco Trust Agent
for Windows
with a dot1x supplicant, and the Cisco Trust Agent for Windows
without a dot1x supplicant. This section focuses on the Cisco Trust Agent with
the dot1x supplicant. The installation packages of the Cisco Trust Agent can be
downloaded from Cisco Connection Online (CCO) at:
http://www.cisco.com
You must have a valid CCO user ID and password to access this information.
When we wrote this book the latest available version was 2.0.1.14. However, for
this book we used Version 2.0.0.30. The installation package consists of a single
executable file: ctasetup-supplicant-win-2.0.0.30.exe. Note that this file is for
Windows XP only.
Refer to the CCO for the latest information about additional platform support.
Note: You can use the CTA with the dot1x supplicant in an L2IP environment,
in the case of future dot1x migration.
Important: If your client is using personal firewall software, even if the service
is disabled, it may block some communication. We recommend leaving the
firewall software running but configuring it to grant Cisco Trust Agent
communication on port 21862/udp if using L2/L3 IP NAC.
This is not necessary
for NAC L2Dot1X.